What is Asymmetric Encryption? Private Key, Public Key
Asymmetric encryption increases the security of the encryption process by utilizing two separate but mathematically related keys known as a public key and a private key. Asymmetric encryption algorithms use a key mathematically related key pair for encryption and decryption. One key of the key pair is is known as the public key and other one is private key.
The private key is possessed only by the user or computer that generates the key pair. The public key can be distributed to any person who wishes to send encrypted data to the private key holder. It is impossible to compute the private key if you know the public key. Hence it is safe to publish the public key.
If the public key is used for encryption, the associated private key is used for decryption.
If the private key is used for encryption, the associated public key is used for decryption
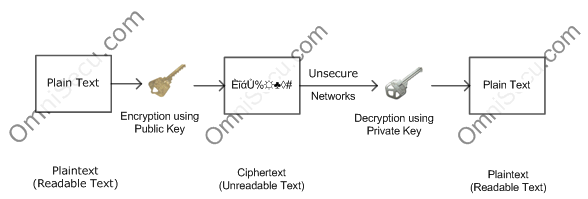
First, the data sender obtains the recipient’s public key. The plaintext is encrypted with asymmetric encryption algorithm, using the recipient’s public key and the ciphertext is created. After the encyprion process, the ciphertext is sent to the recepient through the unsecure network. The recipient decrypts the ciphertext with his private key and now he can access the plaintext from the sender.