Cisco Secure ACS Shell Profiles and Command sets, How to configure Shell Profiles and Command sets in ACS
Cisco Secure ACS Shell Profiles and Command sets are the key terms related with AAA authorization. Cisco Secure ACS Shell profiles and Command Sets are combined for user authorization at shell and also to authorize commands ate different privilege levels and configuration mode.
Cisco Secure ACS Shell Profile is used for defining permissions to be granted for a shell access requests and then for TACACS+ based device administration policy. In a Shell Profile, we can define the "Default Privilege" and the "Maximum Privilege".
Cisco IOS CLI Shell privilege level can be defined in Shell Profiles and the commands for the Privilege Level can be defined in Command Sets. To create a Shell Profile with both "Default Privilege" and "Maximum Privilege" 9 and a Command Set in Cisco Secure ACS, follow these steps.
Step 01 - Connect to Cisco Secure ACS using Microsoft Internet Explorer as shown below. If you are new to AAA, TACACS+ and Cisco Secure ACS, click the following links to learn more.
1) AAA Authentication Authorization and Accounting
2) AAA RADIUS and TACACS+ - Difference between RADIUS and TACACS+
3) Cisco ACS Secure Access Control System Products
4) How to install Cisco ACS (Secure Access Control Server ) 5.4 on VMware Workstation
5) How to connect manage and configure Cisco ACS using web browser
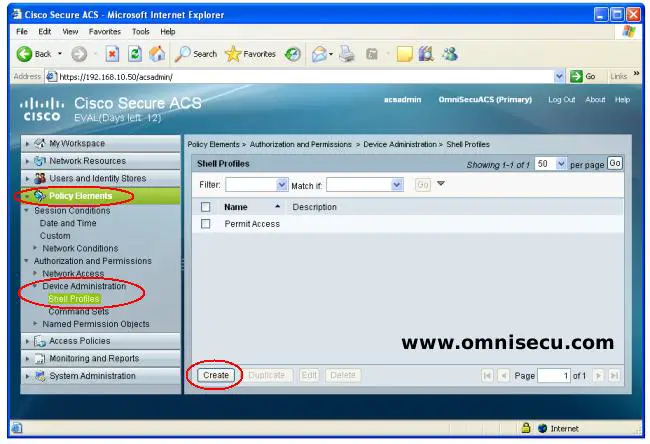
Step 02 - Enter a name and description for the new Shell Profile and then click "Common Tasks", as shwon below.
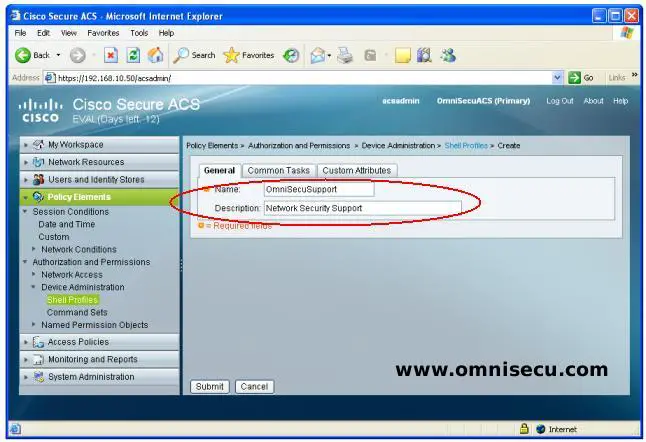
Step 03 - Enter the Default and Maximum Shell Privilege as shown below, and then click "Submit".
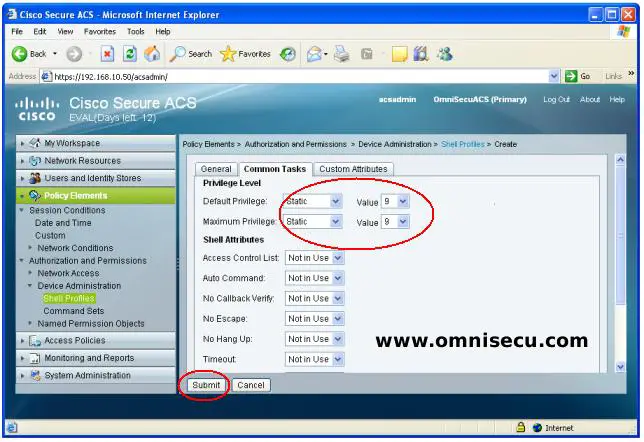
Step 04 - You can see that the Shell profile is created as shown below.
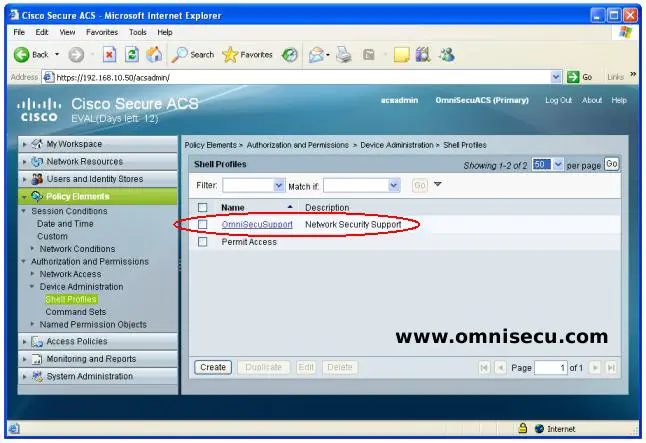
Step 05 - To create a Command Set, open "Policy Elements", "Authorization and Permissions", "Device Administration" and then "Command Sets". Click "Create".
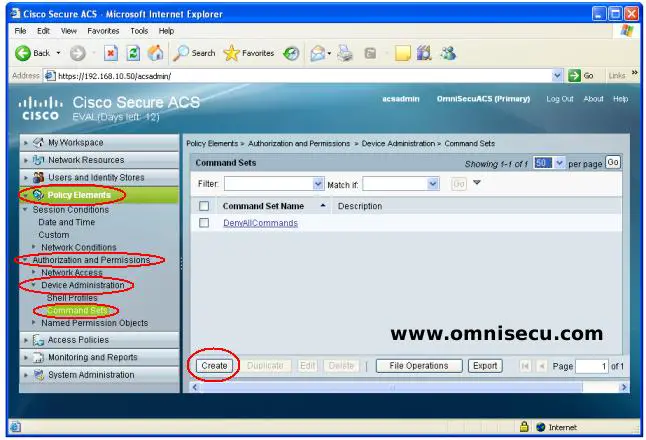
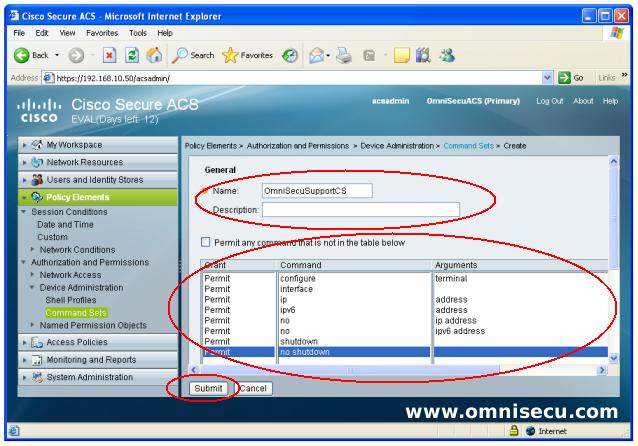
Step 06 - Enter the commands which are required to configure a Cisco Router or Switch interface, as shown below. Click "Submit".
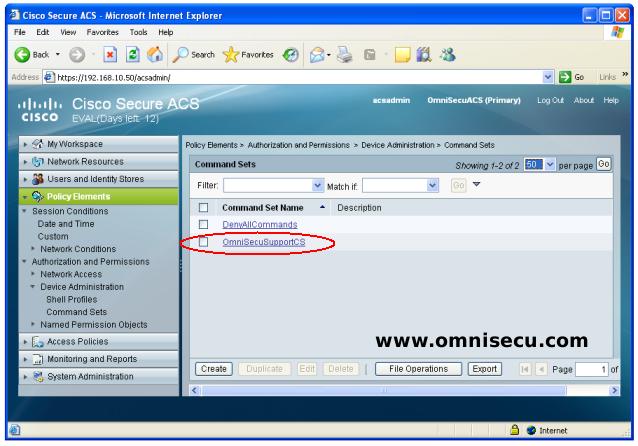
Step 07 - You can see that the new Command Set "OmniSecuSupportCS" is created as shown below.
Step 07 - Now we need to tie up the Shell Profile and Command Set which we created in previous steps to any user for authentication. You need a user created in Cisco Secure ACS for completing this tasks. If you have any doubt in creating an internal user in Cisco Secure ACS, follow these steps to create an internal user in Cisco Secure ACS.
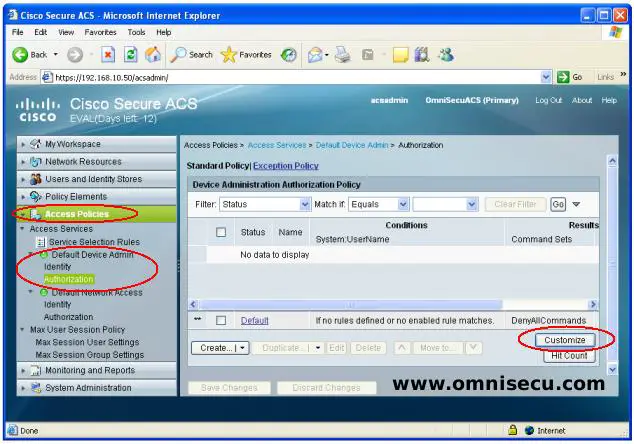
Step 08 - Select "Customize Conditions" and "Customize Results" as shown below. After selecting the "Customize Conditions" and "Customize Results", click the "Create" button as shown in above picture.
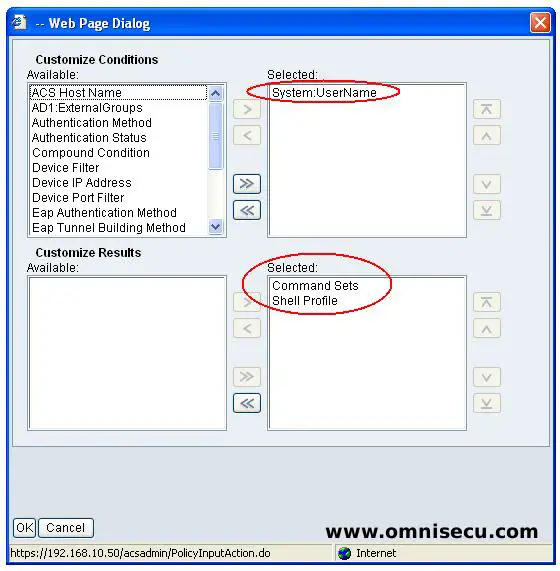
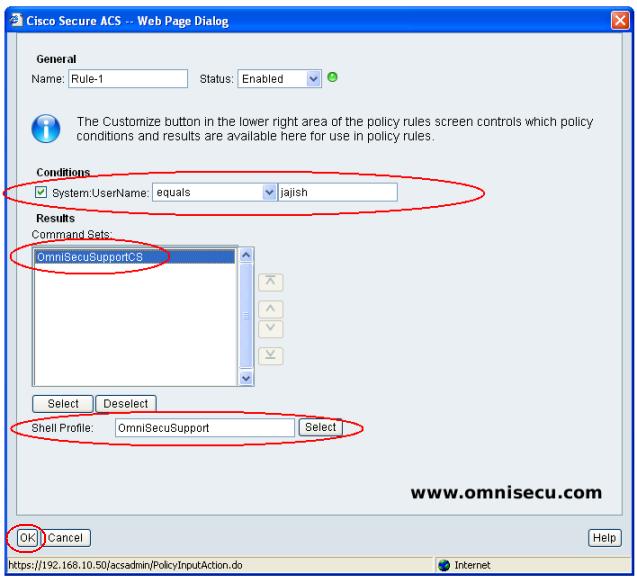
Step 09 - Select the user name (which we created before), Shell Profile and Command Set as shown below, Click "OK" to create Rule, as shown below.
Step 10 - New Access Policy Authorization rule is creates as shown below.
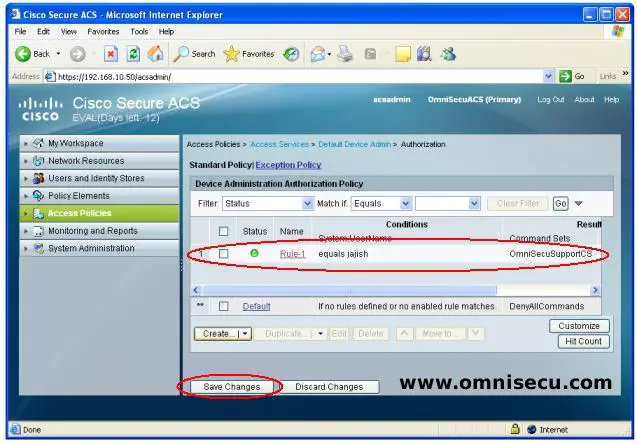
After creating the Authorization Access Policy, you must configure the Cisco Routers and Switches to use AAA Authorization and Accouting using TACACS+ protocol.
Click the following link to learn how to configure Cisco Routers and Switches with AAA Authorization and Accouting using TACACS+ protocol and Cisco Secure ACS.