How to prevent MAC flooding attacks by configuring switchport port-security
Before continuing, visit the following link to learn more about MAC flooding attack
MAC address flooding attack (CAM table flooding attack) is a type of network attack where an attacker connected to a switch port floods the switch interface with very large number of Ethernet frames with different fake source MAC address.
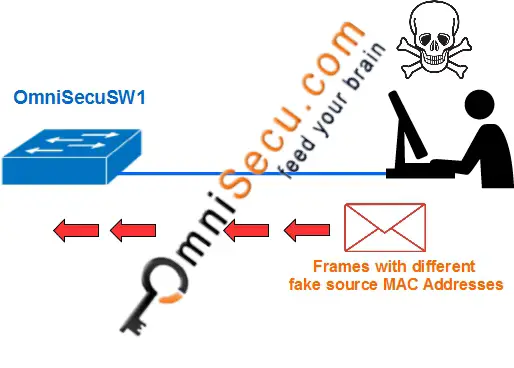
MAC flooding attack can soon drain the memory resources allocated for MAC address table and later the switch will start behaving like a network Hub.
Port Security feature can protect the switch from MAC flooding attacks. Port security feature can also protect the switch from DHCP starvation attacks, where a client start flooding the network with very large number of DHCP requests, each using a different source MAC address. DHCP starvation attacks can result in depletion of available IP addresses in DHCP Server scope.
Port security feature is meant for access ports and it will not work on trunk ports, Ether-channel ports or SPAN (Switch Port Analyzer) ports.
Concepts of Port Security
The goal of Port Security is to prevent a network attacker from sending large number of Ethernet Frames with forged fake source MAC addresses to a Switch interface. This goal is achieved by the following settings, which are related with a switch interface.
1) Enable Port Security Feature. Port security is disabled by default. "switchport port-security" (at interface configuration mode) command can be used to enables Port Security.
OmniSecuSW1(config-if)#switchport port-security
2) Specify a maximum number of MAC addresses allowed on that interface. Remember, it is possible that more that one genuine devices are connected to a switch interface (Example: a phone and a computer).
OmniSecuSW1(config-if)#switchport port-security maximum ? <1-4097> Maximum addresses
3) Define the MAC Addresses of known devices, which are going to access the network via that interface. We can do this by either hardcoding the MAC addresses of known devices (statically define the known MAC addresses) or configure "sticky" MAC Address.
Sticky MAC addresses ("switchport port-security mac-address sticky") will allow us to enter dynamically learned MAC addresses to running config.
The default number of known secure MAC addresses is one.
OmniSecuSW1(config-if)#switchport port-security mac-address ? H.H.H 48 bit mac address sticky Configure dynamic secure addresses as sticky
4) Specify an action to do when a violation occurred on above conditions.
When a violation occurs in switch Port Security, Cisco switches can be configured to act in one of the three options explained below.
Protect: When "protect" option is configured and a violation occurred in switch port security, a switch interface drops frames with an unknown source MAC address after the switch port reaches maximum number of allowed MAC addresses. Frames with known source MAC addresses are allowed. No SNMP trap and a syslog message are generated. The "protect" option is the lowest port security option available.
Restrict: When "restrict" option is configured and a violation occurred in switch port security, a switch interface drops frames with an unknown source MAC address after the switch port reaches maximum number of allowed MAC addresses. The restrict option also sends an SNMP trap and a syslog message and increments a violation counter when a port security violation occurs. Shutdown option sends an SNMP trap and a syslog message also. It also increments a violation counter.
Shutdown: When "shutdown" option is configured and a violation occurred in switch port security, the interface is shut down. Shutdown option sends an SNMP trap and a syslog message also. It also increments a violation counter. Therefore, when a port security violation occurs, the interface is shutdown and no traffic is allowed on that interface. The "shutdown" option is the highest port security option available.
The default violation action is to shut down the port.
OmniSecuSW1(config-if)#switchport port-security violation ? protect Security violation protect mode restrict Security violation restrict mode shutdown Security violation shutdown mode
Following section explains how to configure above concepts of Port Security in a Cisco switch in exact same order.
How to configure port security on a Cisco Switch using "switchport port-security" command
1) To enable port security, use following commands
OmniSecuSW1#configure terminal OmniSecuSW1(config)#interface gigabitethernet 0/0 OmniSecuSW1(config-if)#switchport port-security OmniSecuSW1(config-if)#exit OmniSecuSW1(config)#exit OmniSecuSW1#
2) To specify maximum number of MAC addresses allowed on an interface, use following commands
OmniSecuSW1#configure terminal OmniSecuSW1(config)#interface gigabitethernet 0/0 OmniSecuSW1(config-if)#switchport port-security maximum 5 OmniSecuSW1(config-if)#exit OmniSecuSW1(config)#exit OmniSecuSW1#
3) To define the MAC addresses of known secure devices statically, use following commands
OmniSecuSW1#configure terminal OmniSecuSW1(config)#interface gigabitethernet 0/0 OmniSecuSW1(config-if)#switchport port-security maximum 2 OmniSecuSW1(config-if)#switchport port-security mac-address aaa.bbb.ccc OmniSecuSW1(config-if)#switchport port-security mac-address aaa.bbb.ddd OmniSecuSW1(config-if)#exit OmniSecuSW1(config)#exit OmniSecuSW1#
4) To define the action required when a Port Security violation happened, use following commands
OmniSecuSW1#configure terminal OmniSecuSW1(config)#interface gigabitethernet 0/0 OmniSecuSW1(config-if)#switchport port-security violation shutdown OmniSecuSW1(config-if)#exit OmniSecuSW1(config)#exit OmniSecuSW1#
We can use the "show interface <interface_no>, as shown below to confirm the port is in Errdisable state.
OmniSecuSW1#show interfaces gigabitethernet 0/0
GigabitEthernet0/0 is down, line protocol is down (err-disabled)
How to view the Port Security related settings of an interface
OmniSecuSW1#show port-security interface gigabitethernet 0/0
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 2
Total MAC Addresses : 2
Configured MAC Addresses : 2
Sticky MAC Addresses : 0
Last Source Address : 0000.0000.0000
Last Source Address VlanId : 0
Security Violation Count : 0
OmniSecuSW1#
How to view the secure known MAC addresses configured for Port Security
OmniSecuSW1#show port-security address
Secure Mac Address Table
-------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- -------------
1 0aaa.0bbb.0ccc SecureConfigured Gi0/0 -
1 0aaa.0bbb.0ddd SecureConfigured Gi0/0 -
-------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 1
Max Addresses limit in System (excluding one mac per port) : 4096
OmniSecuSW1#