What is MAC flooding attack and How to prevent MAC flooding attack
MAC address flooding attack (CAM table flooding attack) is a type of network attack where an attacker connected to a switch port floods the switch interface with very large number of Ethernet frames with different fake source MAC address.
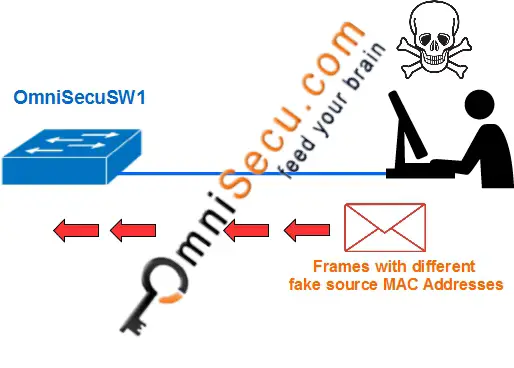
Following images shows a Switch's MAC address table before and after flooding attack.
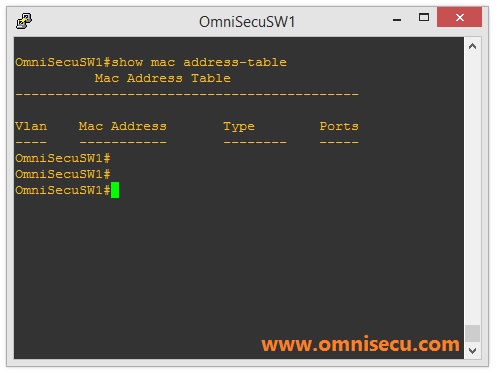
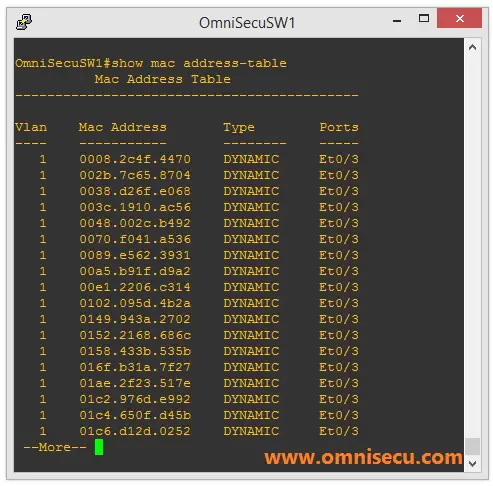
This type of attack is also known as CAM table overflow attack. Within a very short time, the switch's MAC Address table is full with fake MAC address/port mappings. Switch's MAC address table has only a limited amount of memory. The switch can not save any more MAC address in its MAC Address table.
Once the switch's MAC address table is full and it can not save any more MAC address, its enters into a fail-open mode and start behaving like a network Hub. Frames are flooded to all ports, similar to broadcast type of communicaton.
Now, what is the benefit of the attacker? The attacker's machine will be delivered with all the frames between the victim and another machines. The attacker will be able to capture sensitive data from network.
How to prevent MAC flooding attacks
Cisco switches are packed with in-built security feature against MAC flooding attacks, called as Port Security. Port Security is a feature of Cisco Switches, which give protection against MAC flooding attacks.
Visit next lesson to learn How to prevent MAC flooding attacks by configuring port security in Cisco Switches.