IKEv2 Phase 1 (IKE SA) and Phase 2 (Child SA) Message Exchanges
Previous lesson, we had learned about IKEv1 and the IKEv1 message exchanges in Phase1 (Main mode/Aggressive Mode) and Phase2 (Quick Mode). In IKEv1, there are nine message exchanges if IKEv1 Phase 1 is in Main Mode (Six Messages for Main Mode and Three messages for Quick mode) or Six message exchanges if IKEv1 Phase 1 is in Aggressive mode (Three Messages for Aggressive Mode and Three messages for Quick mode).
Internet Key Exchange Version 2 (IKEv2) is the next version of IKEv1. IKEv2 was initially defined by RFC 4306 and then obsoleted by RFC 5996. IKEv2 current RFCs are RFC 7296 and RFC 7427. IKEv2 has most of the features of IKEv1.
Like IKEv1, IKEv2 also has a two Phase negotiation process. First Phase is known as IKE_SA_INIT and the second Phase is called as IKE_AUTH. At the end of second exchange (Phase 2), The first CHILD SA created. CHILD SA is the IKEv2 term for IKEv1 IPSec SA.
At a later instance, it is possible to create additional CHILD SAs to using a new tunnel. This exchange is called as CREATE_CHILD_SA exchange. New Diffie-Hellman values and new combinations of encryption and hashing algorithms can be negotiated during CREATE_CHILD_SA exchange.
IKEv2 runs over UDP ports 500 and 4500 (IPsec NAT Traversal) . Devices configured to use IKEv2 accept packets from UDP ports 500 and 4500.
IKEv2 IPSec Peers can be validated using Pre-Shared Keys, Certificates, or Extensible Authentication Protocol (EAP). Extensible Authentication Protocol (EAP) allows other legacy authentication methods between IPSec peers.
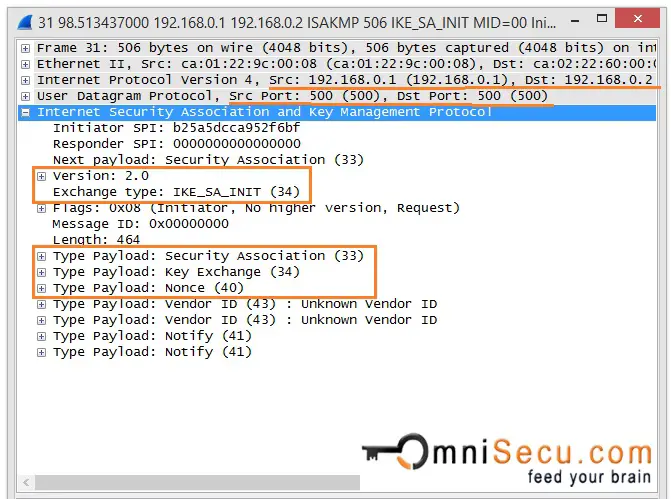
IKEv2 Phase 1 Message 1
In IKEv2, the first message from Initiator to Responder (IKE_SA_INIT) contains the Security Association proposals, Encryption and Integrity algorithms, Diffie-Hellman keys and Nonces.
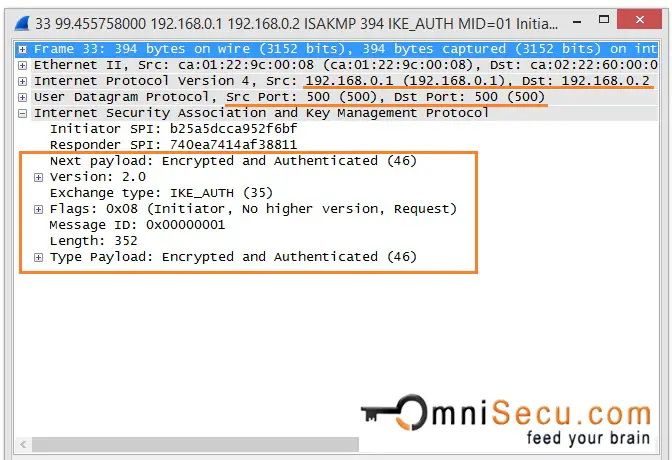
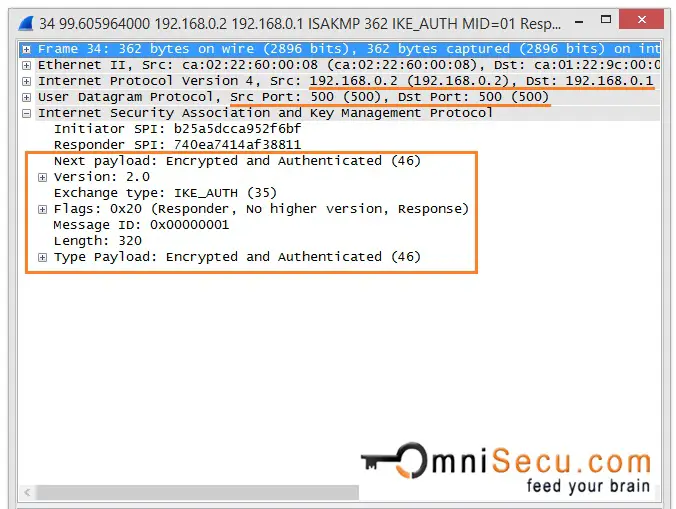
IKEv2 Phase 1 Message 2
In IKEv2, second message from Responder to Initiator (IKE_SA_INIT) contains the Security Association proposals, Encryption and Integrity algorithms, Diffie-Hellman keys and Nonces.
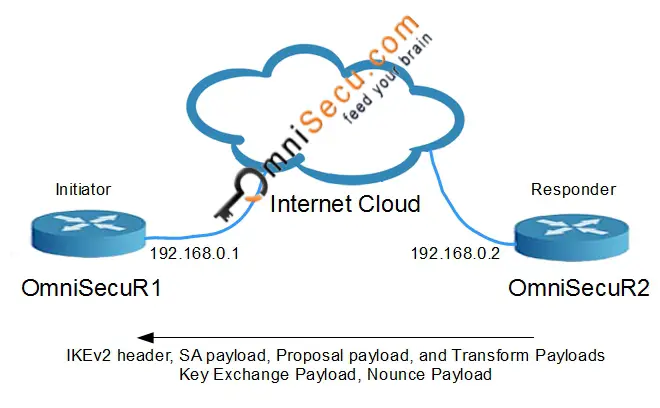
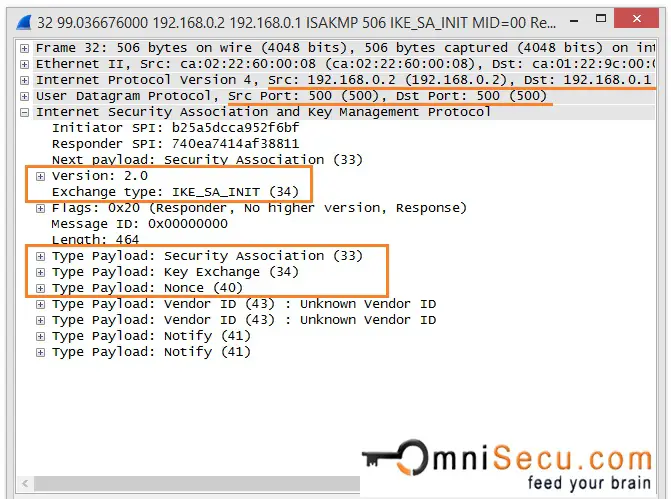
Note that the Messages 1 and 2 are not protected. Now the IPSec peers generate the SKEYSEED which is used to derive the keys used in IKE-SA. All future IKE keys are generated using SKEYSEED. After the Messages 1 and 2, next messages are protected by encrypting and authenticating it.
IKEv2 Phase 1 - Messages 3 and 4
The third and fourth massages (IKE_AUTH) are encrypted and authenticated over the IKE SA created by the previous Messages 1 and 2 (IKE_SA_INIT). These two messages are for Authentication. Initiator's and responders identity, certificates exchange (if available) are completed at this stage. The third and fourth massages (IKE_AUTH) are used authenticate the previous messages, validate the identity of IPSec peers and to establish the first CHILD_SA.
At the end of messages 3 and 4, identities of IPSec Peers are verified and first CHILD_SA is established.