ARP Spoofing attack
Address Resolution Protocol (ARP) spoofing attack is a type of network attack where an attacker sends fake Address Resolution Protocol (ARP) messages inside a Local Area Network (LAN), with an aim to deviate and intercept network traffic.
In normal Address Resolution Protocol (ARP) operation, when a network device sends a ARP request (as broadcast) to find a MAC address corresponding to an IPv4 address, ARP reply comes from the legitimate network device which is configured with the IPv4 address which matches the ARP request. The ARP reply is cached by the requesting device in its ARP table.
A network attacker can abuse Address Resolution Protocol (ARP) operation by responding ARP request, posing that it has the requested IPv4 address. Once the attacker's MAC address is mapped to a authentic legitimate IPv4 address, the attacker will begin receiving any data that is intended for that legitimate IPv4 address. Now the attacker can launch a man-in-the-middle attack can start capturing the network traffic for any sensitive user data.
Attacker can also broadcast Gratuitous ARP message with the IPv4 address of default gateway. Gratuitous ARP is a broadcast packet is used by network devices to announce any change in their IPv4 address or MAC address . By sending Gratuitous ARP message with the IPv4 address of default gateway, attacker can pose as default gateway and capture all the network traffic moving outside the Local Area Network (LAN).
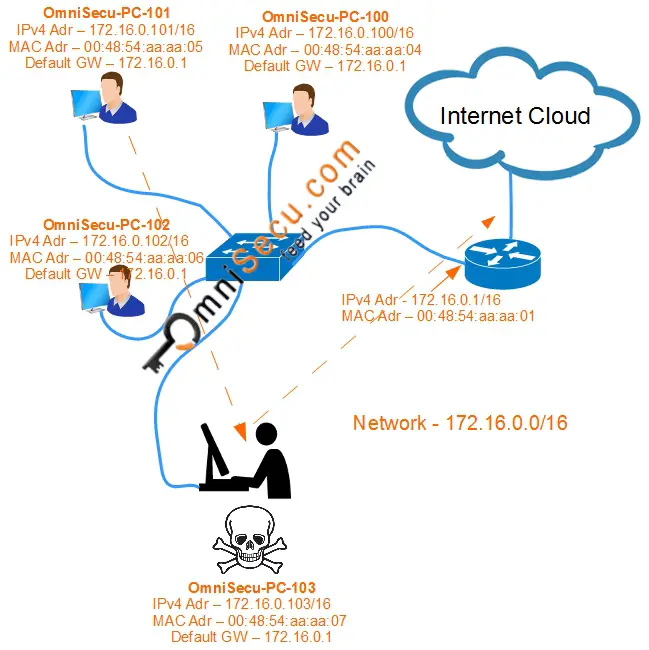
For an example of ARP spoofing attack, consider below topology.
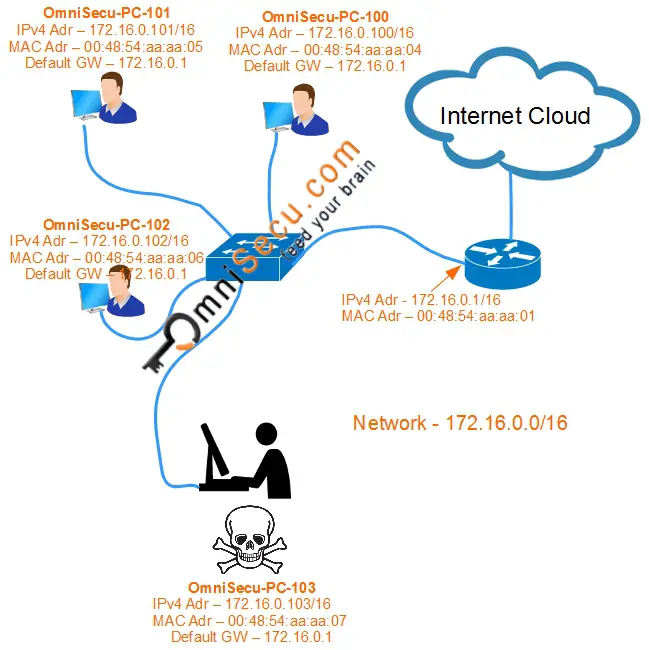
The IPv4 address of the default gateway is 172.16.0.1 and the corresponding MAC Address is 00:48:54:aa:aa:01. The attacker (who is sitting at OmniSecu-PC-103) can broadcast a Gratuitous ARP message with the information that the MAC address corresponding to the IPv4 address of the default gateway (172.16.0.1) is 00:48:54:aa:aa:07 (which is attacker's own MAC address).
This will cause the devices in the network to update their ARP table with a wrong MAC address to IPv4 address mapping. ARP table of the computer has a poisoned mapping of the default gateway IPv4 address 172.16.0.1 to the wrong MAC addresses 00:48:54:aa:aa:07.
The attacker will send ARP messages to the default gateway to deceive the default gateway that the MAC address corresponding to the computer "OmniSecu-PC-101" is 00:48:54:aa:aa:07 (which is attacker's own MAC address).The ARP table of the router also has a poisoned IPv4 address to MAC address mapping. ARP table of the router has a poisoned entry mapping IPv4 address of computer "OmniSecu-PC-101" 172.16.0.101 to the wrong MAC address 00:48:54:aa:aa:07.
Now, whenever computer "OmniSecu-PC-101" sends traffic to the Internet, it will forward the network traffic to the attacker's computer, which it then forwards to the default gateway. Since the attacker is still forwarding the traffic to the Internet via default gateway, "OmniSecu-PC-101" remains unaware that its traffic is being intercepted. Now the attacker can try to capture the traffic for any sensitive user data