Cisco Router/Switch AAA Login Authentication configuration using TACACS+ and RADIUS Protocols through CCP
We have learned in previous lesson (Cisco Router/Switch AAA Login Authentication configuration using TACACS+ or RADIUS protocol through IOS Commands), how to configure Cisco Routers or Switches for AAA login authentication using TACACS+ or RADIUS protocol thorugh Cisco IOS CLI commands. In this lesson, we will discuss how to configure Cisco Routers or Switches for AAA login authentication using TACACS+ or RADIUS protocol thorugh CCP (Cisco Configuration Professional).
Lab Topology
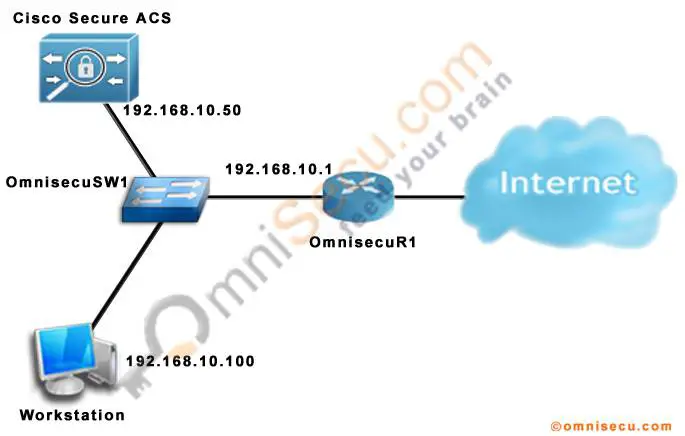
To configure AAA login authentication in a Cisco Router or Switch using TACACS+ or RADIUS protocol using CCP (Cisco Configuration Professional), follow these steps.
Step 1 - Open CCP (Cisco Configuration Professional). Enter the IP address and your user credentials of the Cisco Router or Switch which you want to manage using CCP (Cisco Configuration Professional).
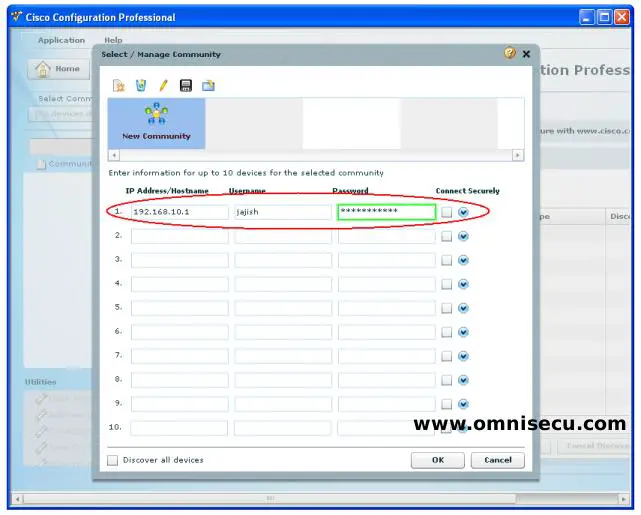
Step 02 - After entering the IP address and user credentials of the Cisco Router or Switch, click "Dicscover" button.
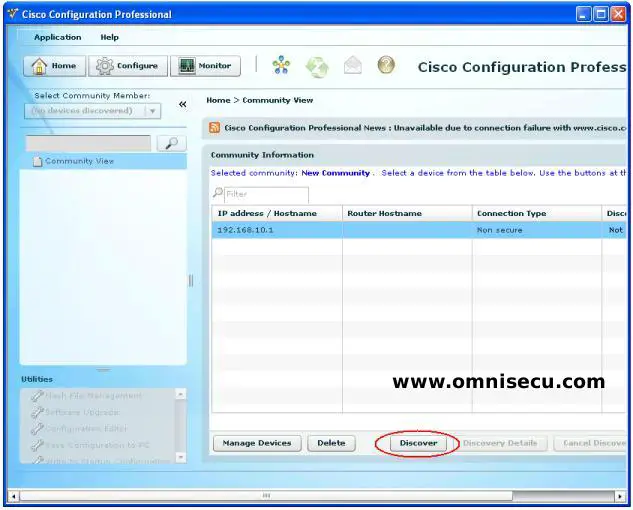
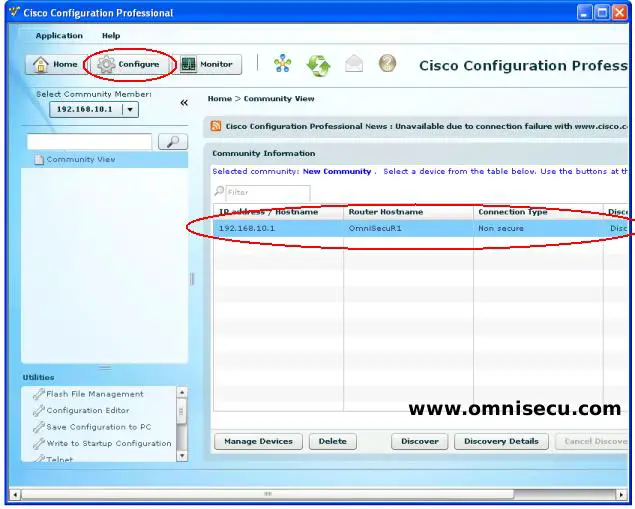
Step 03 - After the Cisco Router or Switch is discovered (OmniSecuR1, in this example), click the "Configure" button, as shown below.
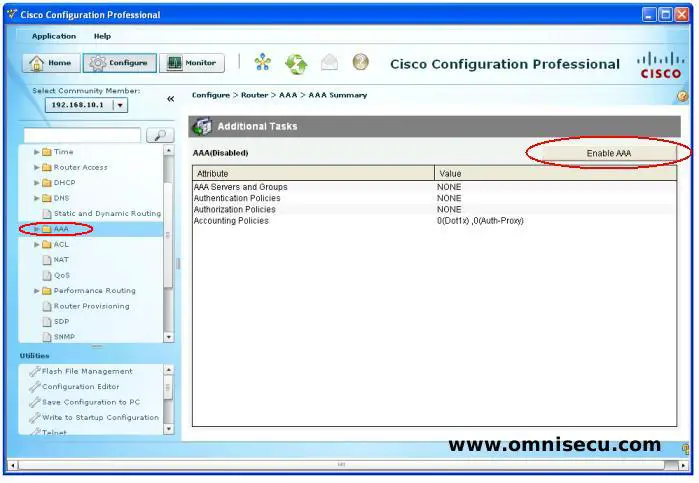
Step 04 - To enable AAA globally in a Cisco Router or Switch, select AAA from the left pane menu and then click "Enable AAA".
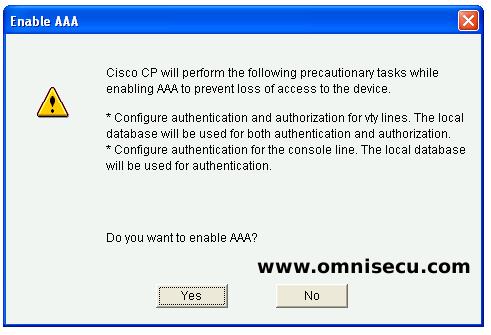
Step 05 - Read the warning message about using local database for authentication and click "Yes" to enable AAA ina a Cisco Router or Switch.
Make sure that you have a local user entry in the local database. If you do not have a local user entry in local device user database, you may not be able to access the device.
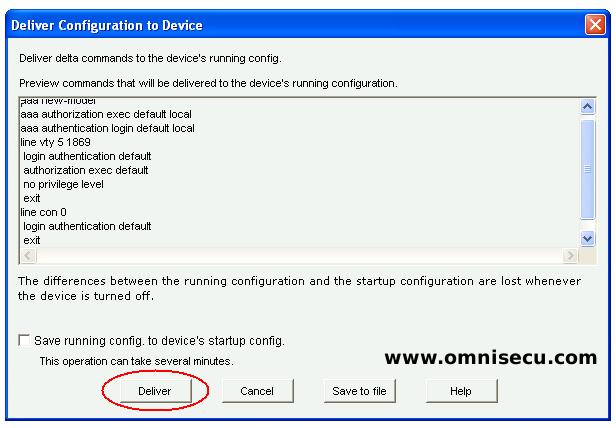
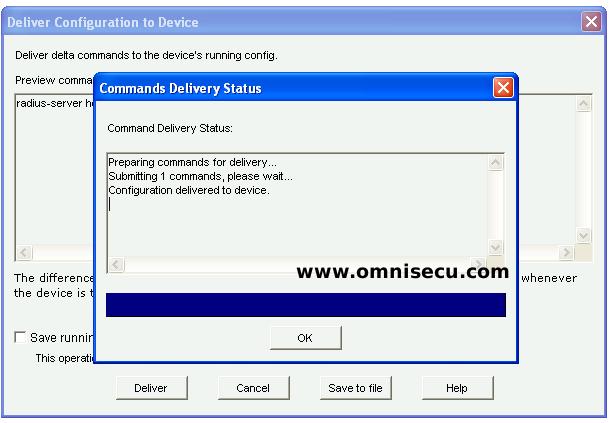
Step 06 - Click the "Deliver" button to deliver the CCP (Cisco Configuration Professional) generated IOS commands to the Cisco Router or Switch. You can also save the Running Configuration to Startup Configuration, by checking the "Save running config. to the device startup config"check box.
Step 07 - You can see the confirmation message, as shown below.
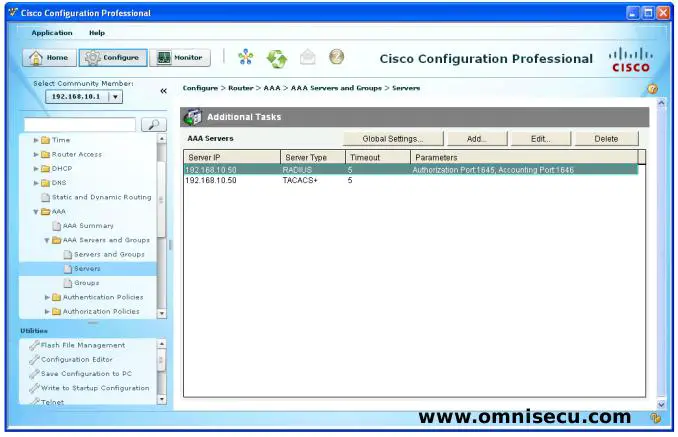
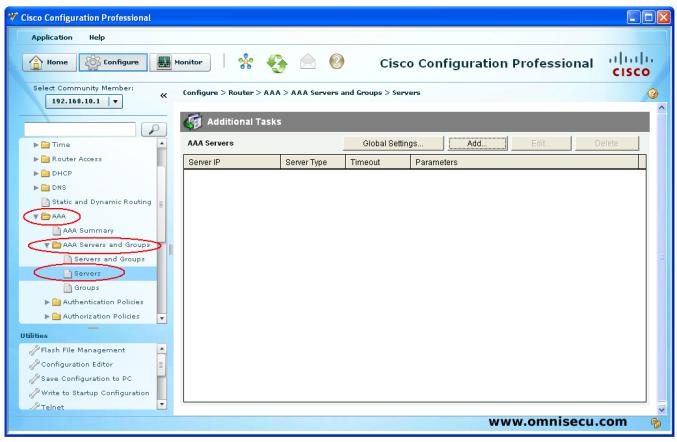
Step 08 - Expand "AAA" tree in CCP (Cisco Configuration Professional), expand "AAA Servers and Groups", and select "Servers" to define a AAA TACACS+ or RADIUS Server.
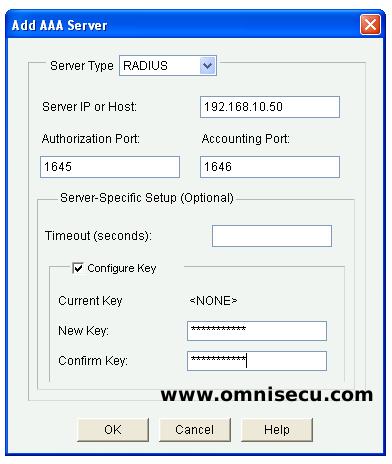
Step 09 - Click "Add" button to define and add a AAA TACACS+ or RADIUS Server. First, for defining a RADIUS Server, select "RADIUS" from combo box. Enter the IP address of Cisco Secure ACS and the Shared Secret key for the AAA client device and the click "OK".
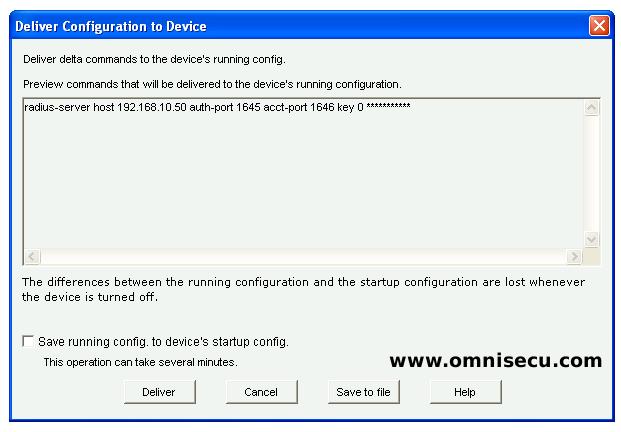
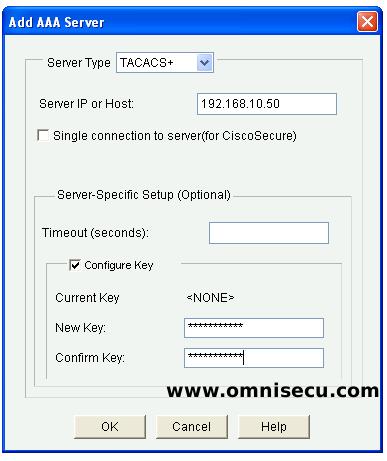
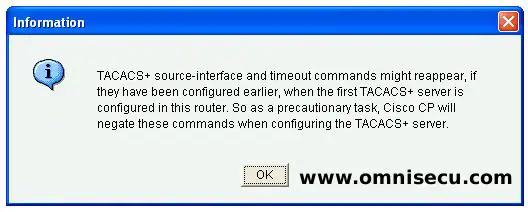
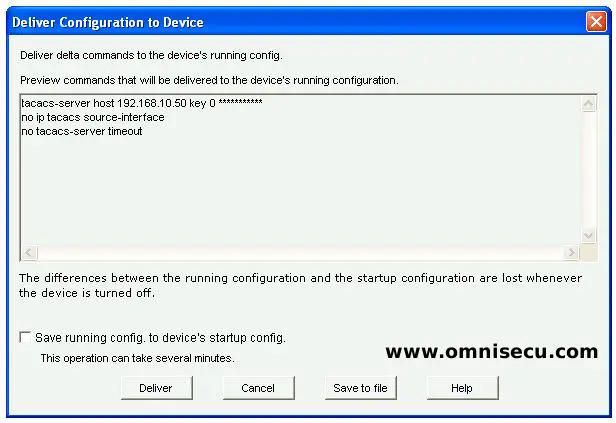
Step 10 - For defining a TACACS+ Server, again click the "Add" button and select "TACACS+" from combo box. Enter the IP address of Cisco Secure ACS and the Shared Secret key for the AAA client device and the click "OK". Accept the information message, click "Deliver" to deliver the CCP (Cisco Configuration Professional) generated IOS commands, and then click "OK" in the command delivery status dialog box.
Step 11 - TACACS+ and RADIUS servers are dedined as shown below.