How to configure Cisco IOS Zone Based Firewall
To configure Cisco IOS Zone Based Firewall, initial step is to create Zones and Zone Pairs. Consider the network topology below.
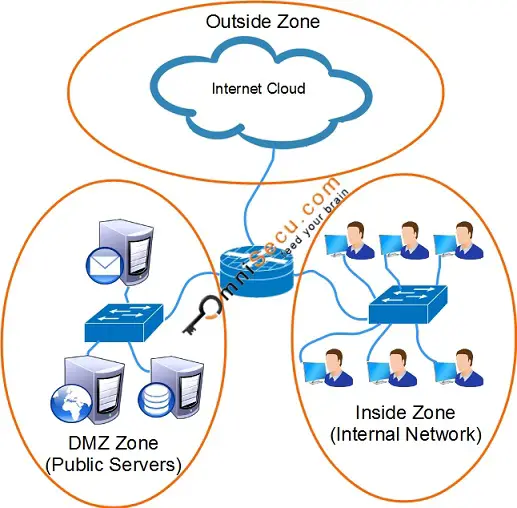
How to create Zones
To create three Zones, "INSIDE", "OUTSIDE" and "DMZ", follow these configuration steps.
OmniSecuR1#configure terminal OmniSecuR1(config)#zone security INSIDE OmniSecuR1(config-sec-zone)#exit OmniSecuR1(config)#zone security OUTSIDE OmniSecuR1(config-sec-zone)#exit OmniSecuR1(config)#zone security DMZ OmniSecuR1(config-sec-zone)#exit OmniSecuR1(config)#exit OmniSecuR1#
How to assign IP addresses and apply interfaces to zones
OmniSecuR1#configure terminal OmniSecuR1(config)#interface gigabitEthernet 0/0 OmniSecuR1(config-if)#ip address 172.16.0.1 255.255.0.0 OmniSecuR1(config-if)#no shutdown OmniSecuR1(config-if)#zone-member security INSIDE OmniSecuR1(config-if)#exit OmniSecuR1(config)#exit OmniSecuR1#
OmniSecuR1#configure terminal OmniSecuR1(config)#interface gigabitEthernet 1/0 OmniSecuR1(config-if)#ip address 192.168.15.1 255.255.255.0 OmniSecuR1(config-if)#no shutdown OmniSecuR1(config-if)#zone-member security DMZ OmniSecuR1(config-if)#exit OmniSecuR1(config)#exit OmniSecuR1#
OmniSecuR1#configure terminal OmniSecuR1(config)#interface gigabitEthernet 2/0 OmniSecuR1(config-if)#ip address 122.175.156.1 255.255.255.0 OmniSecuR1(config-if)#no shutdown OmniSecuR1(config-if)#zone-member security OUTSIDE OmniSecuR1(config-if)#exit OmniSecuR1(config)#exit OmniSecuR1#
Create Zone Pairs and specify the direction of traffic
In this example, we are going to create only one Zone pair, having its direction from "INSIDE" to "OUTSIDE". To create a Zone pair with direction from "INSIDE" to "OUTSIDE", follow these steps.
Please visit the following link to learn what are Zones and Zone Pairs.
OmniSecuR1#configure terminal OmniSecuR1(config)#zone-pair security IN-to-OUT source INSIDE destination OUTSIDE OmniSecuR1(config-sec-zone-pair)#exit OmniSecuR1(config)#exit OmniSecuR1#
How to create Interzone Firewall Access Policy
Cisco IOS Zone Based Firewall Access Policies are made using class maps, policy maps and service policies. Please visit following link to learn what are class maps, policy maps and service policies.
Class maps are used to identify the traffic. To create a class map to match protocols HTTP, HTTPS, FTP and ICMP follow these steps.
OmniSecuR1#configure terminal OmniSecuR1(config)#class-map type inspect match-any OMNISECU-CMAP-IN-to-OUT OmniSecuR1(config-cmap)#match protocol http OmniSecuR1(config-cmap)#match protocol https OmniSecuR1(config-cmap)#match protocol ftp OmniSecuR1(config-cmap)#match protocol dns OmniSecuR1(config-cmap)#match protocol icmp OmniSecuR1(config-cmap)#exit OmniSecuR1(config)#exit OmniSecuR1#
Above configuration steps create a class-map "OMNISECU-CMAP-IN-to-OUT", which matches the network traffic HTTP, HTTPS, FTP, DNS and ICMP.
match-any and match-all are the two configuration parameters used in class-map configuration. match-any is used to match any of the criteria in the class map. match-all is used to match all the criteria in the class map. If we specify match-all in above class-map configuration there will not be a match, because there is no traffic which match HTTP, HTTPS, FTP, DNS and ICMP together.
Policy maps are used to define what we want to do with the traffic identified using Class map. To create a Policy map to inspect the HTTP, HTTPS, FTP DNS and ICMP traffic (which are identified using Class map in previous steps), follow these steps.
OmniSecuR1#configure terminal OmniSecuR1(config)#policy-map type inspect OMNISECU-PMAP-IN-to-OUT OmniSecuR1(config-pmap)#class type inspect OMNISECU-CMAP-IN-to-OUT OmniSecuR1(config-pmap-c)#inspect OmniSecuR1(config-pmap-c)#exit OmniSecuR1(config-pmap)#exit OmniSecuR1(config)#exit OmniSecuR1#
Please note that "inspect" command is used to configure stateful inspection, which will allow the matching return traffic. If stateful inspection is configured, there is no need to create another policy in opposite direction, because the matching traffic is allowed.
Finally, create a service policy and apply the Policy map inside the Zone pair along its direction. Zone based Firewall is uni-directional. To create Service policy, follow these steps.
OmniSecuR1#configure terminal OmniSecuR1(config)#zone-pair security IN-to-OUT s source INSIDE destination OUTSIDE OmniSecuR1(config-sec-zone-pair)#service-policy type inspect OMNISECU-PMAP-IN-to-OUT OmniSecuR1(config-sec-zone-pair)#exit OmniSecuR1(config)#exit OmniSecuR1#f
Some show commands related with Zone based firewall are listed below
OmniSecuR1#show zone security
zone self
Description: System defined zone
zone INSIDE
Member Interfaces:
GigabitEthernet0/0
zone OUTSIDE
Member Interfaces:
GigabitEthernet2/0
zone DMZ
Member Interfaces:
GigabitEthernet1/0
OmniSecuR1#show zone-pair security
Zone-pair name IN-to-OUT
Source-Zone INSIDE Destination-Zone OUTSIDE
service-policy OMNISECU-PMAP-IN-to-OUT
OmniSecuR1#show class-map type inspect
Class Map type inspect match-any OMNISECU-CMAP-IN-to-OUT (id 1)
Match protocol http
Match protocol https
Match protocol ftp
Match protocol icmp
Match protocol dns
OmniSecuR1#show policy-map type inspectf
Policy Map type inspect OMNISECU-PMAP-IN-to-OUT
Class OMNISECU-CMAP-IN-to-OUT
Inspect
Class class-default
Drop