RIP Authentication, RIPv2 Authentication, RIP Authentication Keychain Configuration
Routing Information Protocol Version 1 (RIPv1) doesn’t support authentication. Routing Information Protocol Version 2 (RIPv2) is a Hybrid Routing protocol and RIPv2 allows packets to be authenticated via either an insecure plain text password or a secure MD5 hash based authentication.
For authentication to work in RIPv2, both the sending and receiving routers must be set to use authentication, and must be configured with the same keys. In RIP this is achieved by configuring a key chain in both the routers which require authentication.
The concept of keychain in routing protocol authentication is similar to the normal key chain, which we use to keep our different keys together.

The authentication key chain functionality provides a mechanism for storing a number of different keys for authentication. The main advantage of key chain authentication is that we can change the authentication keys periodically, without causing any network interruption
Every key has an index number and a key string value that is associated it. Key string value associated with a key can be considered as the password for that key.
Each key has a life time mentioned to indicate when that key is valid. The life time of the keys are defined as “send-lifetime” and “accept-lifetime” values.
Very Important: All the Routers running RIPv2 must have the same Date/Time settings for RIPv2 key chain authentication to work properly. It is very difficult to configure all the routers manually to have same date/time settings. This can be achieved by using time synchronization protocol Network Time Protocol (NTP).
The Network Time Protocol (NTP) is used to synchronize the date/time settings of different routers which are running RIPv2 from a Network Time Server.
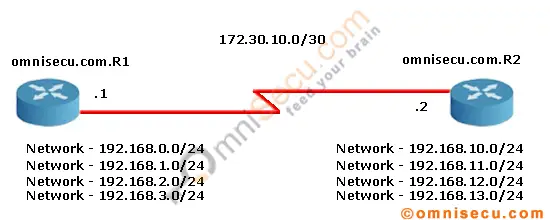
To configure the router interface with an IP address according to the above topology, and then RIPv2, follow these steps.
IP Address and RIPv2 configuration in Router omnisecu.com.R1
IP Address configuration in Router omnisecu.com.R1
omnisecu.com.R1>enable omnisecu.com.R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R1(config)#int s1/0 omnisecu.com.R1(config-if)#ip address 172.30.10.1 255.255.255.252 omnisecu.com.R1(config-if)#no shutdown omnisecu.com.R1(config-if)#exit omnisecu.com.R1(config)#exit omnisecu.com.R1#
RIPv2 configuration in omnisecu.com.R1
omnisecu.com.R1>enable omnisecu.com.R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R1(config)#router rip omnisecu.com.R1(config-router)#version 2 omnisecu.com.R1(config-router)#no auto-summary omnisecu.com.R1(config-router)#network 192.168.0.0 omnisecu.com.R1(config-router)#network 192.168.1.0 omnisecu.com.R1(config-router)#network 192.168.2.0 omnisecu.com.R1(config-router)#network 192.168.3.0 omnisecu.com.R1(config-router)#network 172.30.10.0 omnisecu.com.R1(config-router)#exit omnisecu.com.R1(config)#exit omnisecu.com.R1#
IP Address and RIPv2 configuration in Router omnisecu.com.R2
To configure IP Address in Router omnisecu.com.R2, follow these steps
omnisecu.com.R2>enable omnisecu.com.R2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R2(config)#interface s1/0 omnisecu.com.R2(config-if)#ip address 172.30.10.2 255.255.255.252 omnisecu.com.R2(config-if)#no shutdown omnisecu.com.R2(config-if)#exit omnisecu.com.R2(config)#exit omnisecu.com.R2#
To configure RIPv2 in Router omnisecu.com.R2, follow these steps
omnisecu.com.R2> omnisecu.com.R2>enable omnisecu.com.R2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R2(config)#router rip omnisecu.com.R2(config-router)#version 2 omnisecu.com.R2(config-router)#no auto-summary omnisecu.com.R2(config-router)#network 192.168.10.0 omnisecu.com.R2(config-router)#network 192.168.11.0 omnisecu.com.R2(config-router)#network 192.168.12.0 omnisecu.com.R2(config-router)#network 192.168.13.0 omnisecu.com.R2(config-router)#network 172.30.10.0 omnisecu.com.R2(config-router)#exit omnisecu.com.R2(config)#exit omnisecu.com.R2#
To verify the RIPv2 configuration on router omnisecu.com.R1, run show ip route command from privilaged mode.
omnisecu.com.R1>enable
omnisecu.com.R1#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
R 192.168.12.0/24 [120/1] via 172.30.10.2, 00:00:25, Serial1/0
R 192.168.13.0/24 [120/1] via 172.30.10.2, 00:00:25, Serial1/0
R 192.168.10.0/24 [120/1] via 172.30.10.2, 00:00:25, Serial1/0
172.30.0.0/30 is subnetted, 1 subnets
C 172.30.10.0 is directly connected, Serial1/0
R 192.168.11.0/24 [120/1] via 172.30.10.2, 00:00:25, Serial1/0
C 192.168.0.0/24 is directly connected, Loopback0
C 192.168.1.0/24 is directly connected, Loopback1
C 192.168.2.0/24 is directly connected, Loopback2
C 192.168.3.0/24 is directly connected, Loopback3
To verify the RIPv2 configuration on router omnisecu.com.R2, run show ip route command from privilaged mode.
omnisecu.com.R2#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 192.168.12.0/24 is directly connected, Loopback2
C 192.168.13.0/24 is directly connected, Loopback3
C 192.168.10.0/24 is directly connected, Loopback0
172.30.0.0/30 is subnetted, 1 subnets
C 172.30.10.0 is directly connected, Serial1/0
C 192.168.11.0/24 is directly connected, Loopback1
R 192.168.0.0/24 [120/1] via 172.30.10.1, 00:00:16, Serial1/0
R 192.168.1.0/24 [120/1] via 172.30.10.1, 00:00:16, Serial1/0
R 192.168.2.0/24 [120/1] via 172.30.10.1, 00:00:16, Serial1/0
R 192.168.3.0/24 [120/1] via 172.30.10.1, 00:00:16, Serial1/0
Key chain (OMNISECU_RIP_KEY) in Router omnisecu.com.R1 and omnisecu.com.R1
To configure key chain (OMNISECU_RIP_KEY) in Router omnisecu.com.R1, follow these steps
omnisecu.com.R1>enable omnisecu.com.R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R1(config)#key chain OMNISECU_RIP_KEY omnisecu.com.R1(config-keychain)#key 1 omnisecu.com.R1(config-keychain-key)#key-string PaSSW0rD1 omnisecu.com.R1(config-keychain-key)#send-lifetime 00:00:00 Jan 10 2013 00:00:00 Mar 10 2013 omnisecu.com.R1(config-keychain-key)#accept-lifetime 00:00:00 Jan 10 2013 00:00:00 Mar 10 2013 omnisecu.com.R1(config-keychain-key)#exit omnisecu.com.R1(config-keychain)#key 2 omnisecu.com.R1(config-keychain-key)#key-string PaSSW0rD2 omnisecu.com.R1(config-keychain-key)#send-lifetime 23:50:00 Mar 9 2013 00:00:00 Sep 10 2013 omnisecu.com.R1(config-keychain-key)#accept-lifetime 23:50:00 Mar 9 2013 00:00:00 Sep 10 2013 omnisecu.com.R1(config-keychain-key)#exit omnisecu.com.R1(config-keychain)#exit omnisecu.com.R1(config)#exit omnisecu.com.R1(config)#exit omnisecu.com.R1#
To configure key chain (OMNISECU_RIP_KEY) in Router omnisecu.com.R2, follow these steps
omnisecu.com.R2>enable omnisecu.com.R2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R2(config)#key chain OMNISECU_RIP_KEY omnisecu.com.R2(config-keychain)# key 1 omnisecu.com.R2(config-keychain-key)# key-string PaSSW0rD1 omnisecu.com.R2(config-keychain-key)#$:00:00 Jan 10 2013 00:00:00 Mar 10 2013 omnisecu.com.R2(config-keychain-key)#$0:00 Jan 10 2013 00:00:00 Mar 10 2013 omnisecu.com.R2(config-keychain-key)# key 2 omnisecu.com.R2(config-keychain-key)# key-string PaSSW0rD2 omnisecu.com.R2(config-keychain-key)#$:50:00 Mar 10 2013 00:00:00 Sep 10 2013 omnisecu.com.R2(config-keychain-key)#$0:00 Mar 10 2013 00:00:00 Sep 10 2013 omnisecu.com.R2(config-keychain-key)#exit omnisecu.com.R2(config-keychain)#exit omnisecu.com.R2(config)#exit omnisecu.com.R2#
After creating the key chain, the next step is to configure authentication mode (plain text or MD5) (at interface level) and to configure the interface to use key chain for RIPv2 authentication (at interface level).
In RIPv2, we have to modes of authentication. 1) Plain Text authentication (Not secure) and 2) MD5 Authentication (Secure).
Follow the first part if you require only plain text authentication and follow the second part if you require MD5 authentication.
Plain Text (insecure) Authentication
To configure plain text (insecure) authentication in Router omnisecu.com.R1 interface serial 1/0 using key chain (OMNISECU_RIP_KEY), we created previous step, follow these steps
omnisecu.com.R1>enable omnisecu.com.R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R1(config)#interface serial 1/0 omnisecu.com.R1(config-if)#ip rip authentication mode text omnisecu.com.R1(config-if)#ip rip authentication key OMNISECU_RIP_KEY omnisecu.com.R1(config-if)#exit omnisecu.com.R1(config)#exit omnisecu.com.R1#
To configure plain text (insecure) authentication in Router omnisecu.com.R2 interface serial 1/0 using key chain (OMNISECU_RIP_KEY), we created previous step, follow these steps
omnisecu.com.R2>enable omnisecu.com.R2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R2(config)#interface serial 1/0 omnisecu.com.R2(config-if)#ip rip authentication mode text omnisecu.com.R2(config-if)#ip rip authentication key OMNISECU_RIP_KEY omnisecu.com.R2(config-if)#exit omnisecu.com.R2(config)#exit omnisecu.com.R2#
MD5 (secure) Authentication
To configure MD5 (secure) authentication in Router omnisecu.com.R1 interface serial 1/0 using key chain (OMNISECU_RIP_KEY), we created previous step, follow these steps
omnisecu.com.R1>enable omnisecu.com.R1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R1(config)#interface s1/0 omnisecu.com.R1(config-if)#ip rip authentication mode MD5 omnisecu.com.R1(config-if)#ip rip authentication key-chain OMNISECU_RIP_KEY omnisecu.com.R1(config-if)#exit omnisecu.com.R1(config)#exit omnisecu.com.R1#exit
To configure MD5 (secure) authentication in Router omnisecu.com.R2 interface serial 1/0 using key chain (OMNISECU_RIP_KEY), we created previous step, follow these steps
omnisecu.com.R2> omnisecu.com.R2>enable omnisecu.com.R2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. omnisecu.com.R2(config)#interface s1/0 omnisecu.com.R2(config-if)#ip rip authentication mode MD5 omnisecu.com.R2(config-if)#ip rip authentication key-chain OMNISECU_RIP_KEY omnisecu.com.R2(config-if)#exit omnisecu.com.R2(config)#exit omnisecu.com.R2#