How to associate IPSec filter list to IPSec filter action
This lesson will teach you how to associate the IPSec IP filter list you have created in the previous lesson to an IPSec filter action. This filter action will block all Telnet traffic to the domain controller SERV03.omnisecu.com.
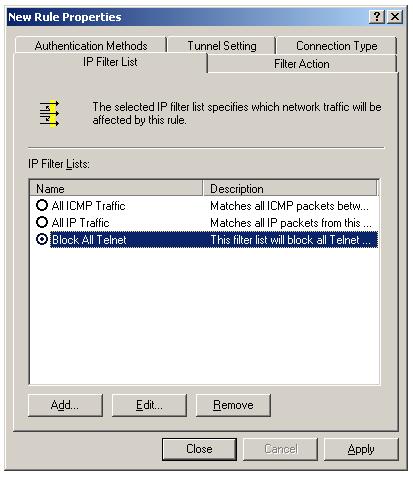
We have created a IPSec filter list "Block All Telnet" which filter all Telnet traffic originating from any IP address to the domain controller SERV03.omnisecu.com. We need to associate a filter action "Block" with this filter list. when any traffic matches "Block All Telnet" filter list arrives at the domain controller, it will be blocked.
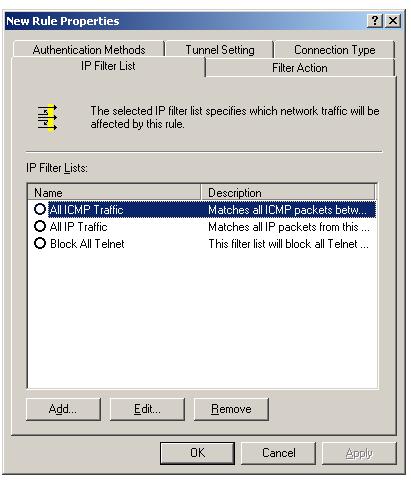
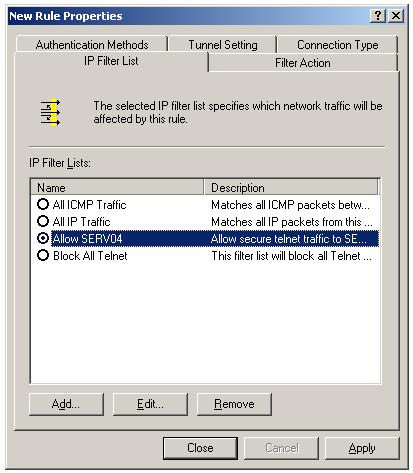
Select the new filter list "Block All Telnet" you have created in last lesson by selecting the radio button.
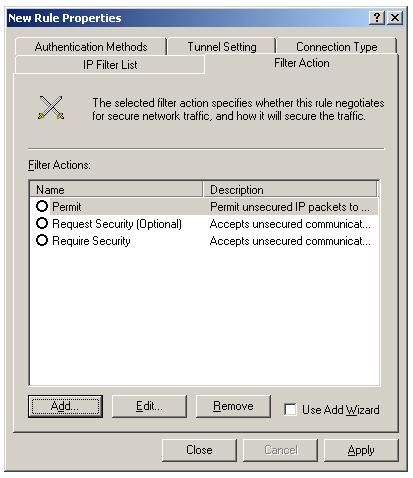
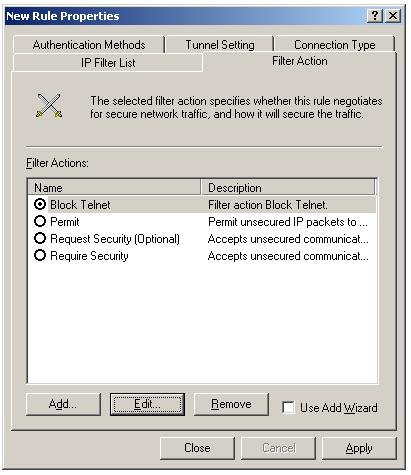
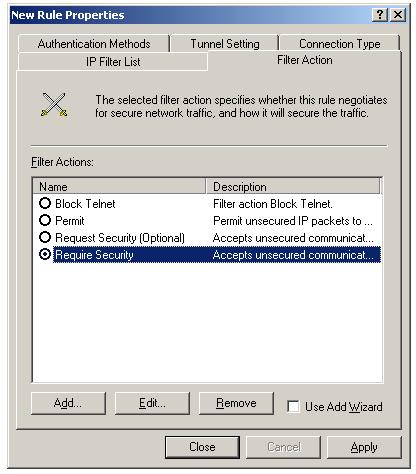
Now click the filter action tab, to associate a filter action with this filter list.
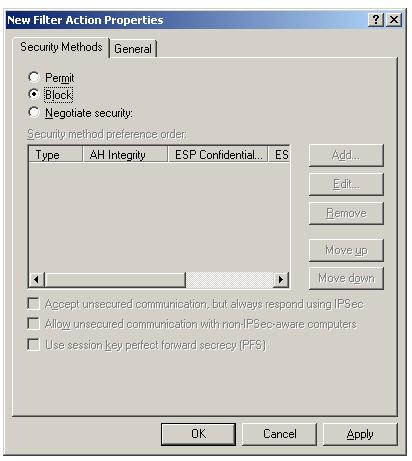
To add IPSec block filter action, Uncheck the "Use Add Wizard" and Click "Add". Select "Block" radio button inside "New Filter Action Properties".
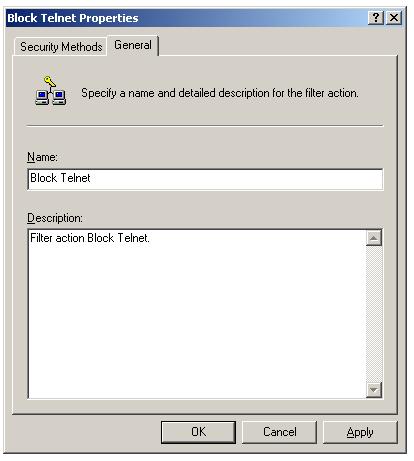
Click "General" tab, enter a meaning-ful name for the filter action, and a description.
Click "OK".
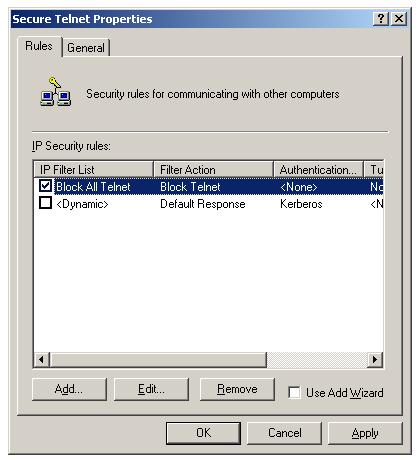
New filter action "Block Telnet" will be listed, select it by clicking the radio button. Click "Apply" and "Close". You can see the new "Block All Telnet" rule listed in the Rules tab of the IPSec policies.
New IPSec rule is created. There are three more tabs in the rule properties dialog box.
1) Authentication Methods - Lists the IPSec authentication methods. Three possible authentication methods are
Kerberos: Kerberos 5 is the default authentication method in a Windows Server 2003 domain. Users running the Kerberos protocol within a trusted domain can authenticate using this method.
Certificates: Digital certificates can be used for authentication, if a trusted certificate authority is available.
Shared Key: A Pre-shared key can be used for authentication when kerberos is not available. A pre-shared key is a string value which is configured on each computer and must be the same on both computers.
2) Tunnel Setting - Specifies whether this is in Tunnel mode or Transport mode. You need to specify the end-point of the tunnel also. "This rule does not specify an IPSec tunnel" option is the Transport mode.
3) Connection Type - Determines for which types of connections the rule will be applied: LAN, Remote Access, or All Network Connections.
You have created a IPSec rule to block all telnet traffic to the domain controller. Now you need create a IPSec rule allowing SERV04.omnisecu.com to allow secure telnet access. Follow the steps we did before except a few changes.
Click the "Add" tab in the Secure Telnet IPSec policy to add a new rule.
Click "Add" button in the "New Rule Properties" dialog box, to add an IPSec IP filter list.
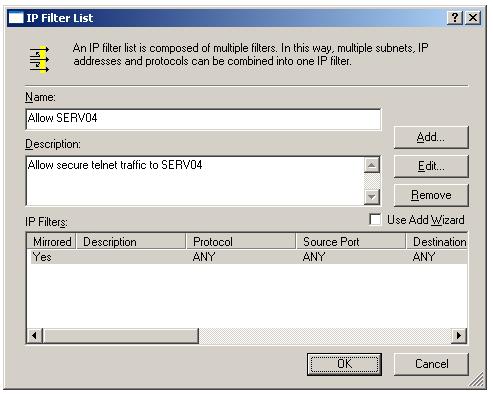
Type a meaning-ful name and description for the IPSec IP filter list.
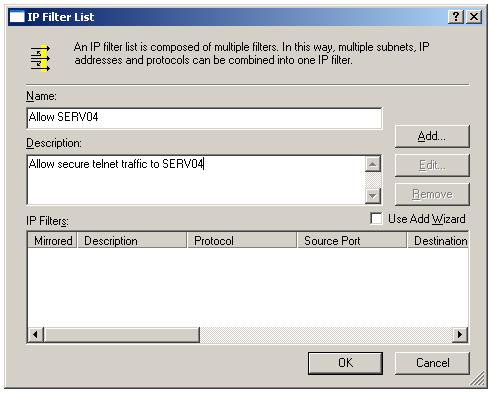
Click "Add" button to add an IPSec IP filter.
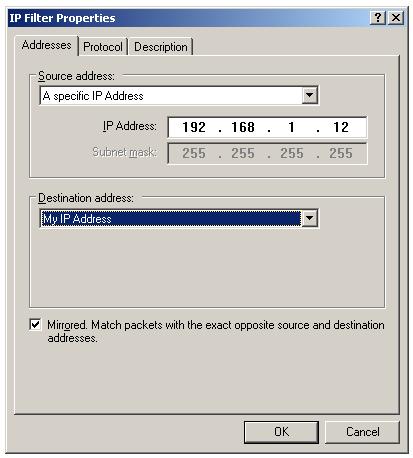
Select "A specific IP Address" from the combo box of Source address and enter the IP address od SERV4.omnisecu.com (192.168.1.12), to which we need to enable secure telnet communication using IPSec. Enter Destination address as "My IP address". Click Protocol tab.
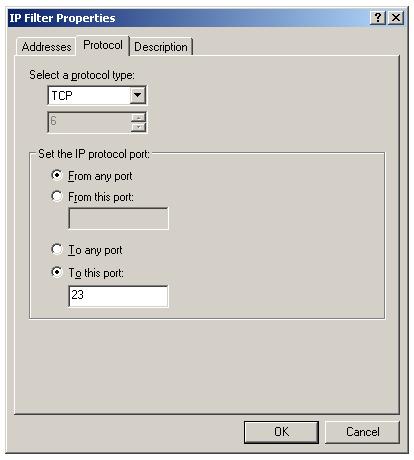
Enter the protocol and port nunmber to enable secure traffic.
Click "OK".
Select the new filter list "Allow SERV04" and click filter action tab.
Select "Require Security" filter action to enable secure IPSec communication between SERV03.omnisecu.com and SERV04.omnisecu.com. Click "Apply" and "Close". Refer next lesson how to configure IPSec encryption algorithm, hashing algorithm and other settings.
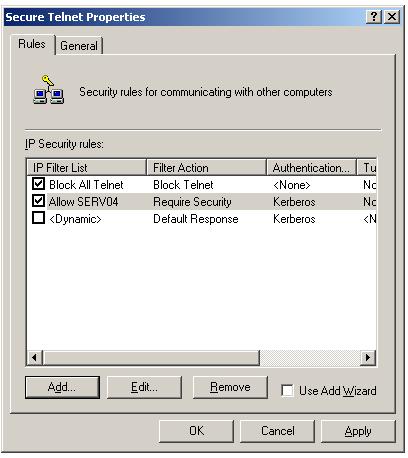
The two rules you have created are listed in the "Secure Telnet" policy properties.
At this point you may wondering about these two conflicting rules. "Block all Telnet" rule is defined to block all telnet traffic to the domain controller SERV03.omnisecu.com and "Allow Serv04" is defined to allow secure telnet traffic from SERV04.omnisecu.com. The IPSec rules are automatically ordered from the most specific to the least specific. Here "Allow SERV04" IPSec rule is most specific, because we have specified the IP address of SERV04.omnisecu.com (192.168.1.12).
You have learned how to associate an IPSec IP filter list with a filter action. You have created two rules, one rule will block all IP traffic and other rule enable secure Telnet traffic betwee SERV03.omnisecu.com and SERV04.omnisecu.com. Click "Next" to continue.