What is a Digital Certificate?
The data structure used to transport and validate keys is called a digital certificate. A certificate protects the key by guaranteeing the identity of the issuer, the identity of the owner, and the purposes for which the key can be used. A certificate cannot be forged because the issuing authority digitally signs it. The signature is applied to a hash of the certificate. This enables clients to validate the issuer's identity and find any alteration. The client decrypts the hash using the issuer's public key and then compares the result to a separate hash it performs on the certificate. If the results match, the certificate is valid.
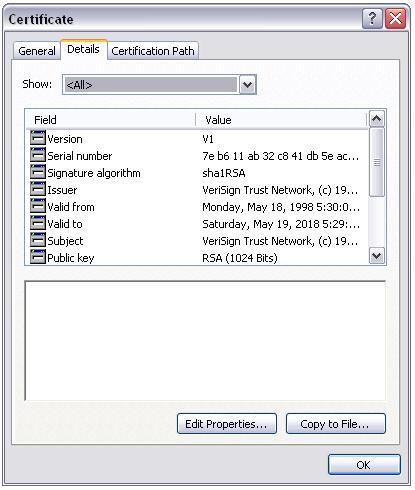
A Digital Certificate contains the following fields (some are optional).
Issued By: The Certification Authority (CA) that issued the digital certificate.
Issued To: The recipient that obtained the digital certificate. If the recipient is a user, the name can be the user's logon ID, User Principal Name (UPN), or Distinguished Name (DN).
Intended Uses (OID): A certificate has one or more uses. This shows the intended uses of the certificate.
Version: The certificate version. Windows Certification Authority (CA) servers issue X.509 Version 3 certificates.
Serial Number: This is a sequential number assigned by the CA to the certificate. The number is unique and acts as a validity check.
Signature Algorithm: The hashing algorithm used to do the digital signature for the certificate. This is typically either SHA-1 or MD5.
Issuer: This is the X.500 distinguished name of the issuing server.
Valid From: This is the issue date of the certificate.
Valid To: This important field defines the expiry date of the certificate.
Subject: This is the X.500 distinguished name of the certificate's owner.
Public Key: This field contains the public key.
CA Version: This field contains the version number (number of times the authorization certificate for a particular Certification Authority (CA) has been renewed).
Subject Key Identifier: This field contains an SHA-1 hash of the Public Key field used to uniquely identify the contents. This prevents alteration of the public key.
Certificate Template: This field is a Microsoft extension that contains name of the template used by the CA to generate this certificate.
Key Usage: This field contains the OIDs of the purposes for the certificate.
Authority Key Identifier: Contains an SHA-1 hash of the public key of the issuing CA along with the distinguished name of the CA.
CRL Distribution Points (CDPs): CRL (Certificate Revocation List) information listed by LDAP path, URL, and file share name.
Authority Information Access: Information for a client to find the certificate of the issuing CA.
Thumbprint: A hash of the certificate.
Thumbprint Algorithm: The algorithm used to obtain the certificate hash.