How Hash Values can be used to determine Integrity of Data
The term Data Integrity in network security is used mention the accuracy of Data in network. The Data in network traffic MUST NOT be altered while in network. In other words, the Data which is received by the recipient must be exactly same as the Data sent from the Sender. Hashing Algorithms can be used to verify the integrity of Data.
Let me explain (with an example) how we can use Hash Values to determin the Integrity of Data. There are many free tools available in internet to find Hash Values of data. One of such tool is File Checksum Integrity Verifier, which is a free download from Microsoft. FCIV is a command line tool, which supports MD5 and SHA-1 Hash Value calculation. Click the following link to download file checksum integrity verifier.
After downloading the file, extract it to a folder. There are two files in "C:\jajish" folder. One is fciv.exe binary file and other is a text file, "data-integrity-check.txt".
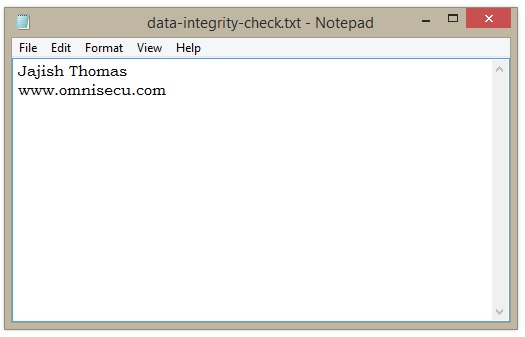
The text content of the text file "data-integrity-check.txt" is shown below.
Now, we will find the MD5 Hash Value of above text file "data-integrity-check.txt" using fciv.exe tool, as shown below.
Step 1: Open command prompt and move to the folder where you had extracted fciv.exe tool. Run the command as shown below.
Step 2: Note the output of the above command as shown below.
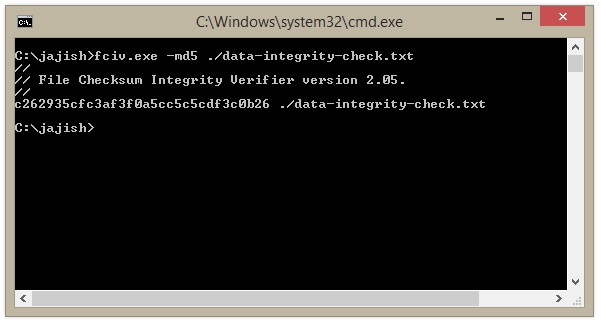
The Hash Value calculated is c262935cfc3af3f0a5cc5c5cdf3c0b26
Step 3: Now make some changes in the original file, by just adding a period (.) at the end of www.omnisecu.com., and save. Note that the original file is altered by just a character.
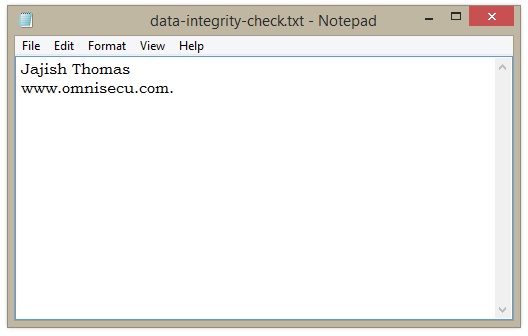
Step 4: After the change in the original file is saved, again compute the Hash Value using fciv.exe as shown below.

Step 5: New Hash Value is entirely different from the first hash value, as shown below.
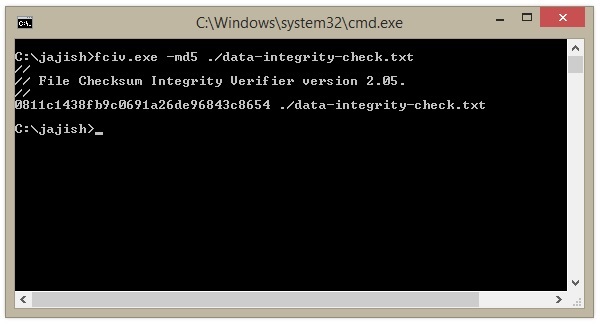
The new Hash Value computed by the fciv.exe tool is 0811c1438fb9c0691a26de96843c8654, which is entirely different from the previous one c262935cfc3af3f0a5cc5c5cdf3c0b26, which shows that the original Data is altered and Data Integrity is compromised.
Security protocols like IPSec make use of Hash Values to identify any change happened to original Data.