Encrypted Data Recovery
Encrypting File System (EFS) provides data recovery capability to recover encrypted files if the user is not available or user keys are not available.
As we learned before, there are two ways in which the file can be decrypted.
1) Using the private key of the corresponding public key used in the encryption process.
2) Using the private key of the corresponding public key of the Data Recovery Agent (DRA) who is designated before the file is encrypted.
When a recovery policy is in place, all File Encryption Keys (FEKs) are additionally wrapped with the recovery agent public keys. The encrypted File Encryption Keys (FEKs) are stored in the Data Recovery Field (DRF). If both the above mentioned keys are not available, data recovery is not possible.
If the user who encrypted the file is not available, you can reset the user's password in Active Directory and then log on as the user to decrypt the file. If resetting the user's password is not an option, you can still open the user's encrypted files using private key of the Data Recovery Agent (DRA). The default Data Recovery Agent (DRA) is the domain Administrator account.
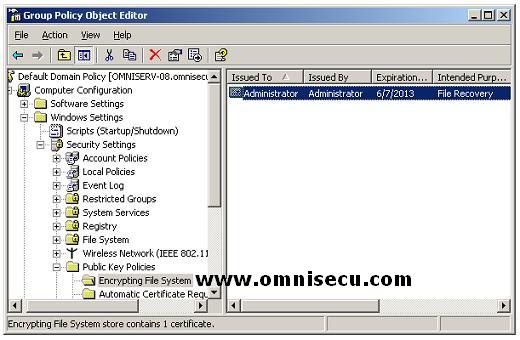
Encrypting File System (EFS) clients get a copy of the Data Recovery Agent's (DRA) public key as an X.509 certificate, which is stored in a domain group policy. To view this certificate, open the domain group policy and open Computer Configuration > Windows Settings > Security Settings > Public Key Policies. A screenshot of the above group policy node is copied below.
When an Active Directory domain member computer starts up, it downloads the Data Recovery Agent’s (DRA) Certificate from the Domain Controller. The member caches the certificate in the local Registry and it can use the Data Recovery Agent (DRA) certificate even it is disconnected from the network.
If the user is not available, Data Recovery Agent (DRA) can recover (open) the encrypted files with his private certificate. If the Data Recovery Agent (DRA) (The default Data Recovery Agent (DRA) is the domain Administrator account) log on to a desktop, he cannot open the encrypted files because the private key of the Data Recovery Agent (DRA) is kept in the Administrator profile on the first Domain Controller of the domain.
If the System Administrator want to decrypt the files, without changing the user's password, the following methods are ideal.
1) You can export the key from the Domain Controller and then import the key to the certificate store of the desktop or member server and decrypt the encrypted files. After decrypting the files, you should delete the private key from the certificate store.
2) You can copy the encrypted files to a machine where the private key of the Data Recovery Agent (DRA) is available and decrypt it there.