How IEEE 802.1X (dot1x) Port Based Authentication works
Visit following link to learn what is IEEE 802.1X (dot1x) Port Based Authentication, Supplicant, Authenticator and Authentication Server if you are not familiar with IEEE 802.1X (dot1x) Port Based Authentication.
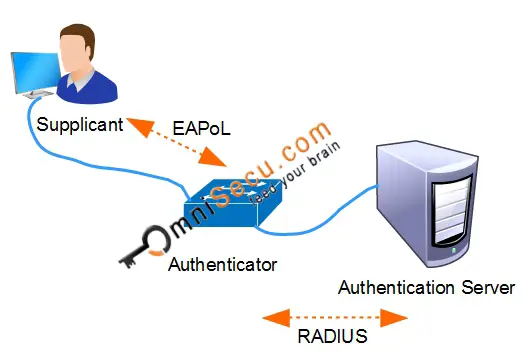
IEEE 802.1X (dot1x) uses the Extensible Authentication Protocol (EAP) to exchange messages during the authentication process. In a wired Ethernet LAN, EAPoL (Extensible Authentication Protocol (EAP) over LAN) is used to transport EAP packets between Supplicant and an Authenticator over Local Area Network (LAN). Before authentication, the identity of the endpoint is unknown and all traffic is blocked except EAPoL. Once the user credentials are successfully verified, other user traffic is permitted.
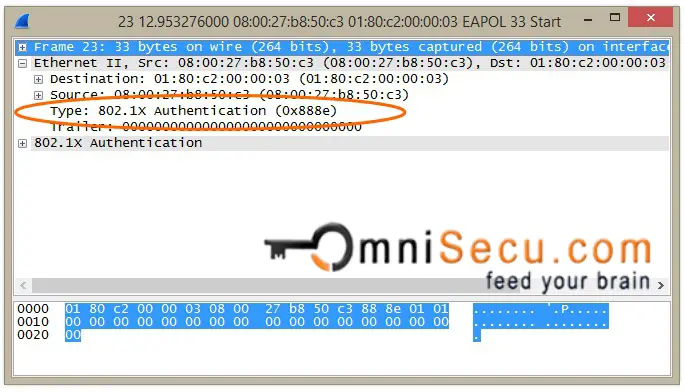
EAPoL frames have Ether Type of 0x888e.
In IEEE 802.1X (dot1x), Extensible Authentication Protocol (EAP) provides a way for the Supplicant and the Authenticator to negotiate an EAP authentication method. EAP method is used to define the credential type and how the credentials are submitted from the Supplicant to the Authentication Server.
Extensible Authentication Protocol (EAP) is "extensible" by adding new EAP methods. Different EAP methods are available for use in conjunction with IEEE 802.1X (dot1x). Common EAP methods used in 802.1X (dot1x) are EAP-TLS (EAP-Transport Layer Security) and PEAP-MSCHAPv2 (Protected EAP-Microsoft Challenge Handshake Authentication Protocol version 2).
The protocol used for communication between Supplicant and Authenticator is EAPoL. The protocol used for communication between Authenticator and Authentication Server is RADIUS.
IEEE 802.1X (dot1x) Authentication Process
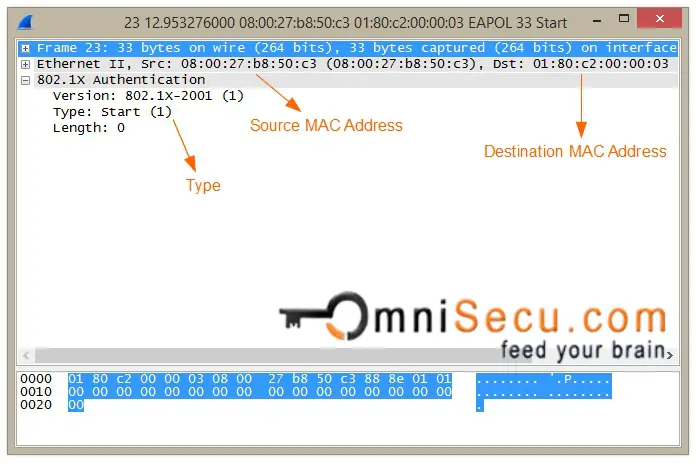
Step 01: The first step of IEEE 802.1X (dot1x) Authentication Process is an EAPoL-Start message. When the Supplicant first connects to the LAN, it will send EAPoL-Start message to a multicast group (special destination multicast MAC address 01:80:c2:00:00:03) to identify the Authenticator.
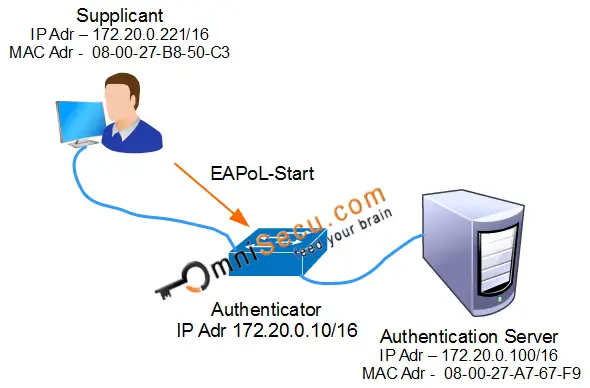
EAPoL-Start message wireshark capture is shown below.
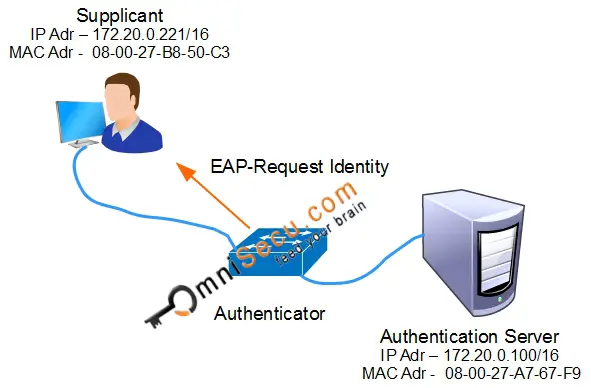
Step 02: Athenticator will send back EAP-Request Identity message (in response to the EAPOL-Start message), which is used to request identity from the Supplicant, for example, user name. Authenticator sends out EAP-Request Identity periodically, even before receiving an EAPoL-Start message.
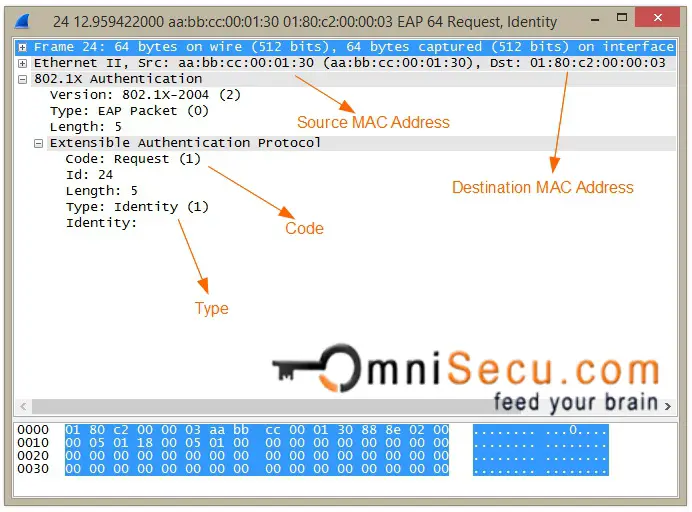
EAP-Request Identity message wireshark capture is shown below.
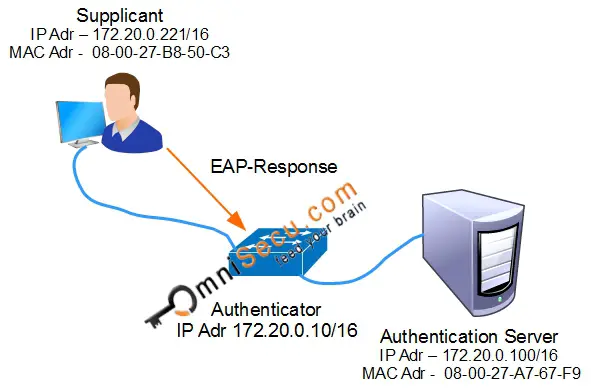
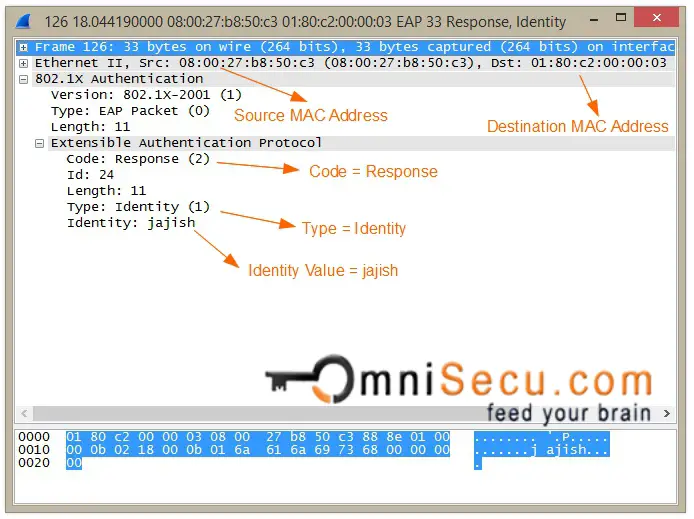
Step 03: As a response to EAP-Request Identity message, the Supplicant provides its identity (example user name) in an EAP-Response message to the Authenticator (in this case, switch).
EAP-Response message wireshark capture is shown below.
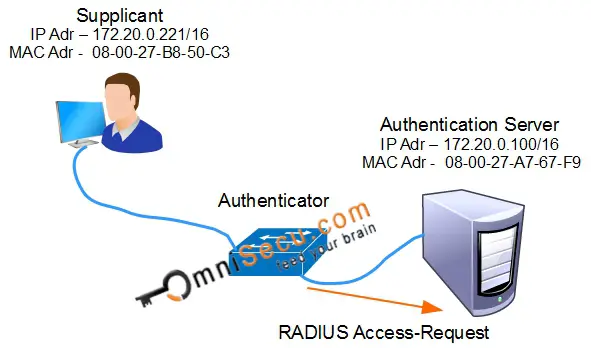
Step 04: The Authenticator forwards the information received from the Supplicant to the Authentication Server (RADIUS server, in this case). The protocol used for communication between Supplicant and Authenticator is EAPOL protocol, and the protocol used for communication between Authenticator and Authentication Server is RADIUS protocol.
Note that RADIUS uses UDP as transport layer protocol and uses port numbers 1812 for authentication and 1813 for accounting (also UDP port number 1645 is used for authentication and 1646 for accounting).
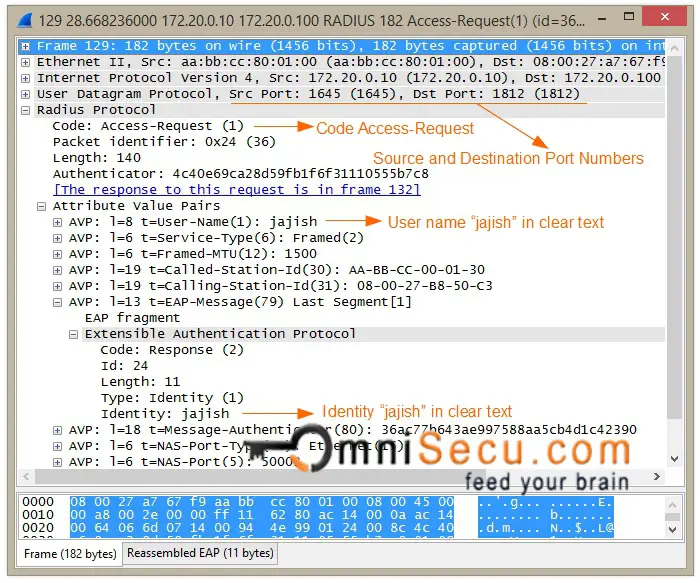
The Authenticator (Network Switch) will create a RADIUS Access-Request message and forward that message to the Authentication Server.
RADIUS Access-Request message wireshark capture is shown below.
Step 05: Once the Authentication Server (RADIUS Server) received the Access-Request RADIUS message, the Authentication Server (RADIUS Server) will send back a RADIUS Access-Challenge message to the Authenticator (Network Switch). The Access-Challenge message from the server contains not only the challenge, but also the authentication method to be used for further communication. The Supplicant can reject the authentication method and request another which the Supplicant supports.
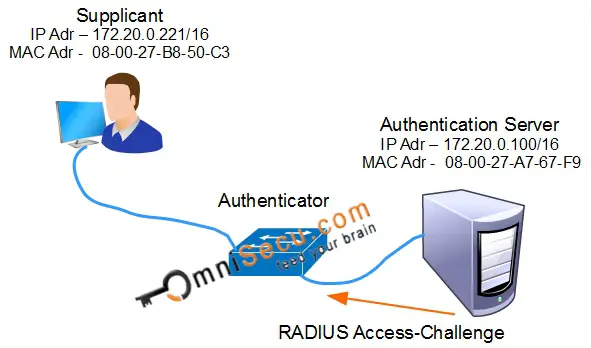
RADIUS Access-Challenge message wireshark capture is shown below.
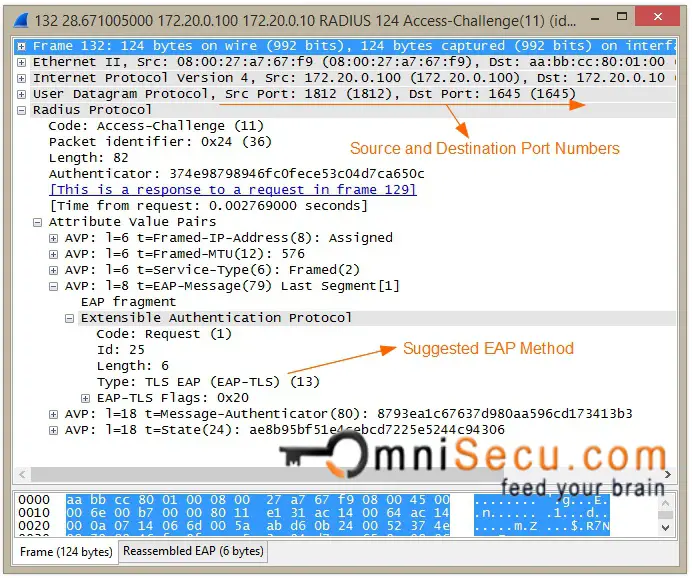
Step 06: The Authenticator receives the Access-Challenge message from Authentication Server. The Authenticator (Network Switch) will now prepare a EAP-Request Message (called as EAP-Request Auth) and forward that message to the Supplicant. The purpose of this EAP-Request message is to verify that the Supplicant can support the EAP method suggested by the Authentication Server (RADIUS Server). In tthis case the suggested EAP method is EAP-TLS, which you can see inside above packet capture screen shot.
EAP-Request message wireshark capture is shown below.
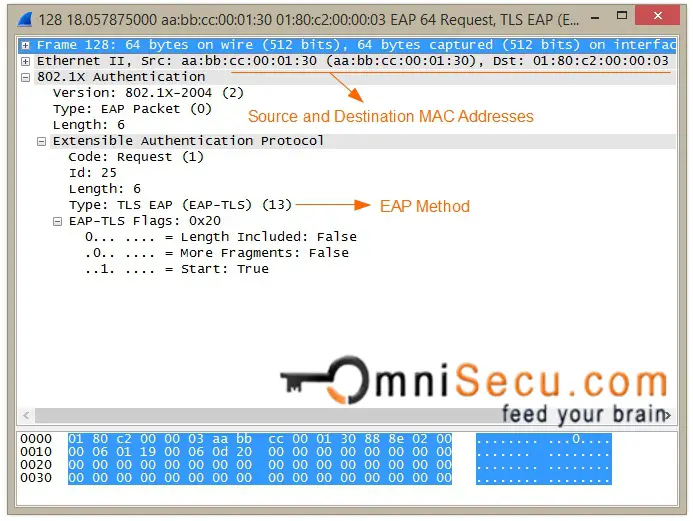
Step 07: If the Supplicant software is not configured to support suggested EAP method (in this case EAP-TLS), the Supplicant can reject the EAP authentication method and request another EAP method. The Supplicant can request another EAP method by sending an EAP-Response Auth NAK message which also specifies the EAP authentication method the Supplicant wants to use.
EAP-Response NAK message wireshark capture is shown below.
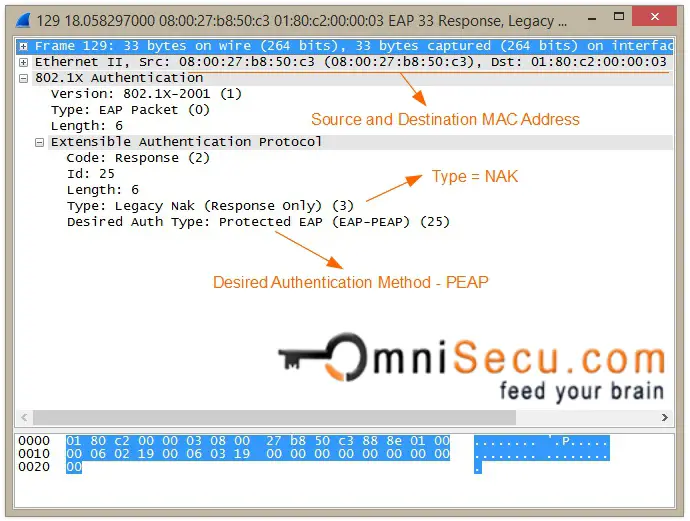
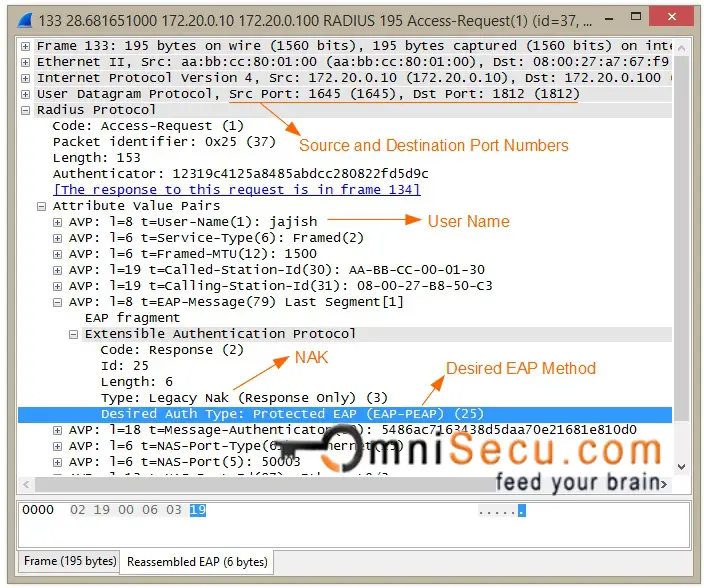
Step 08: Authenticator will forward the EAPoL NAK message and the desired Authentication method sent from the Supplicant to the Authentication Server (RADIUS Server) as RADIUS Access-Request message. Now the Authentication Server (RADIUS Server) can start the Authentication process based on desired Authentication Method.

RADIUS Access-Request message wireshark capture is shown below.
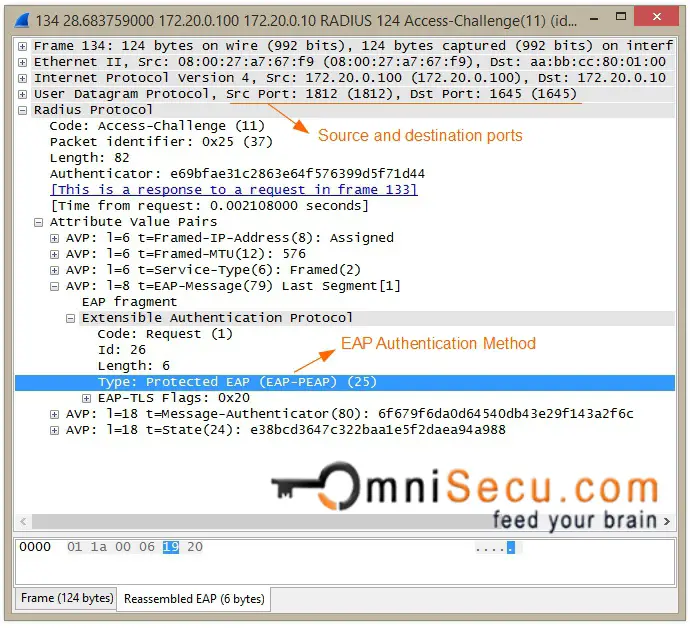
Step 09: The Authentication Server will now send back a new Access-Challenge message, based on the EAP authentication method supported by the Supplicant. Once the EAP Authentication method is agreed by Supplicant and Authentication Server, a few more messages are exchanged, which are related with the agreed EAP Authentication method. Those messages are omitted here in this lesson.

RADIUS Access-Challenge message wireshark capture is shown below.
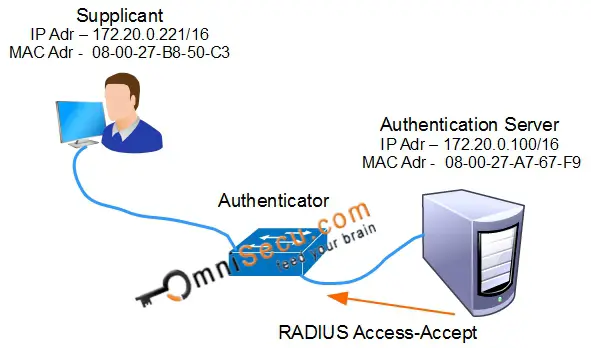
Step 10: When the credentials of the user are successfully verified by Authentication Server after PEAP authentication process, the Authentication Server will send a RADIUS Access-Accept message to the Authenticator (Network Switch).
If the credentials are wrong, the Authentication Server will send a RADIUS Access-Reject message to the Authenticator (Network Switch).
RADIUS Access-Accept message indicates that the user request is valid and RADIUS Access-Reject message indicates that this user request is invalid.
RADIUS Access-Accept message wireshark capture is shown below.
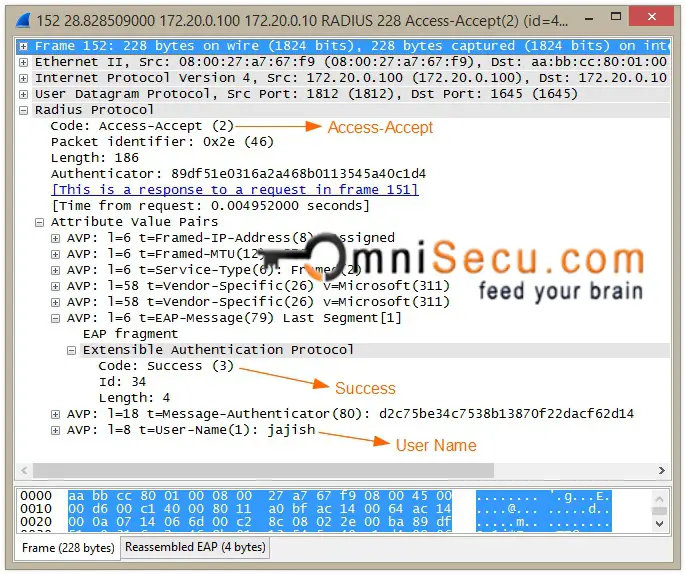
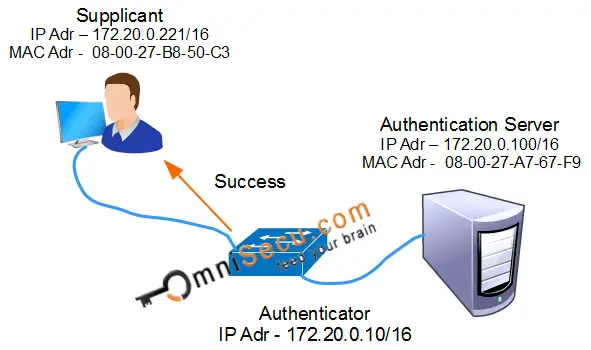
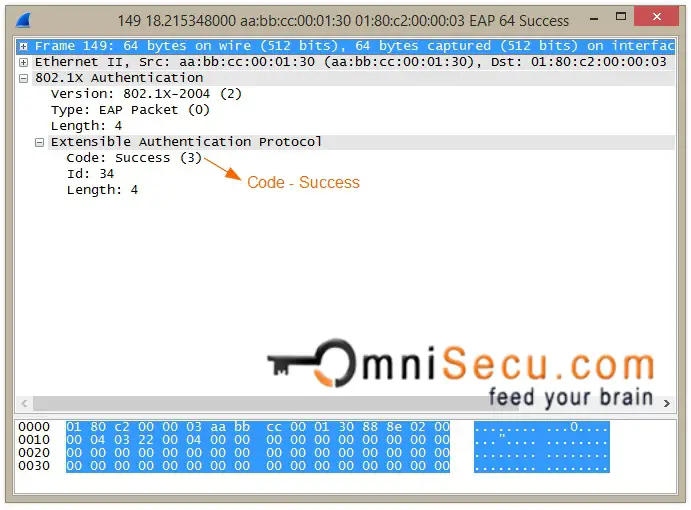
Step 11: Once the Authenticator receive RADIUS Access-Accept from Authentication Server, the Authenticator will send back a EAP Success message to Supplicant as shown below. The switch port will be open for the client for network communiation.
EAP Success message capture screen shot is copied below.
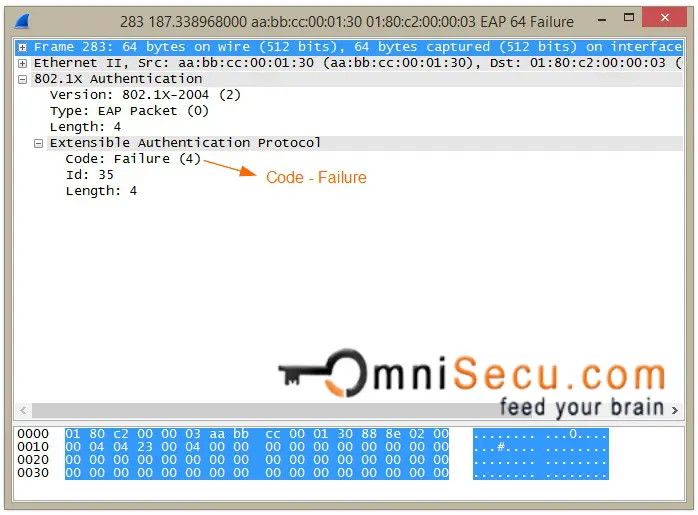
If there is a problem in evaluating the the credentials of the user, the Authenticator will send back a EAP Failure message to the Supplicant as shown below.