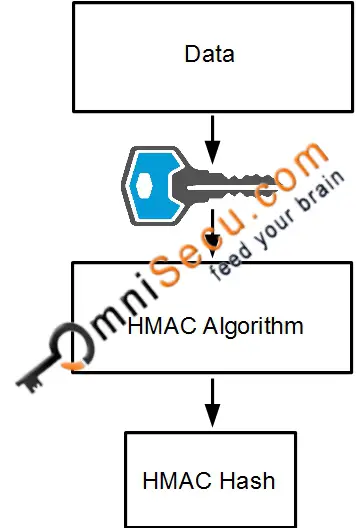
What is HMAC (Hashed Message Authentication Code)
We had learned about Hash Values and important Hash Value Algorithms in previous lessons. We also learned how Hash Values can be used to determin Data integrity. Unfortunately, Hash values in its original form are not capable to protect the integrity of data. If an attacker alter the Data and the Hash Value together in transmission, it will become impossible to detect the Data is tampered. A simple hash value, in its original form is not enough to protect a message from tampering.
Hashed Message Authentication Code (HMAC) is a hash function created using a Shared Secret key. Since HMAC is created using Shared Secret (which is only available to IPSec peers), a hacker cannot alter the Data and create new HMAC hash in-between the transmission. Hashed Message Authentication Code (HMAC) can be used to verify the integrity and authenticity of Data transmissions.
IPSec uses Hashed Message Authentication Code (HMAC) to protect the Hash values. RFC 4868 defines various HMAC functions related with IPSec.