How to configure Site-to-Site IPSec VPN using IKEv1 (Main Mode) using Pre-shared Key Authentication
If you are new to the basic concepts of VPN (Virtual Private Network) and IPSec, please learn following lessons before continuing.
What is VPN (Virtual Private Network)
What is IPSec and Why we need IPSec
Important Technical Terms Related with IPSec
What are the terms Encryption, Decryption, Clear-Text and Cipher-Text
What are the terms Symmetric Encryption and Assymetric Encryption
Important Symmetric and Assymmetric Encryption Algorithms
What are Hash values? Important Hash value Algorithms
How Hash Values can be used to determine Integrity of Data
What is HMAC (Hashed Message Authentication Code)
What is Diffie-Hellman Key Exchange
Main Components of IPSec - IKE, ESP and AH
IPSec VPN Modes - Tunnel Mode and Transport Mode
Security Association and Security Parameter Index
IKEv1 Main Mode, Aggressive Mode and Quick mode Message Exchanges
What is Perfect Forward Secrecy (PFS)
IKEv2 Phase 1 (IKE SA) and Phase 2 (Child SA) Message Exchanges
What is NAT-Traversal (Network Address Translation - Traversal)
Site-to-Site IKEv1 IPSec VPN Configuration - Lab Topology
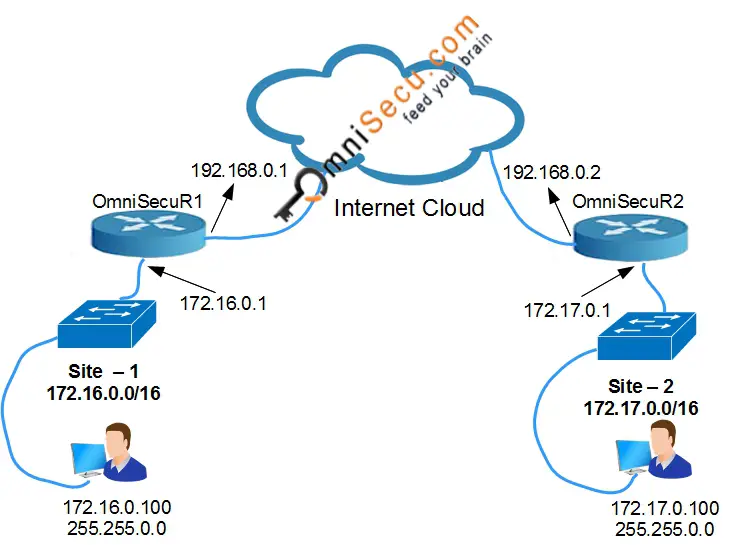
Before proceeding, make sure that all the IP Addresses of your network devices are configured correctly. Make sure that routing is configured correctly. Make sure you can reach all the devices by pinging all IP Addresses.
Step 1: Configure Host name and Domain name in IPSec peer Routers
• To configure Hostname on OmniSecuR1 use the following commands.
Router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)#hostname OmniSecuR1 OmniSecuR1(config)#exit OmniSecuR1#
• To configure Domain name on OmniSecuR1, use the following commands.
OmniSecuR1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR1(config)#ip domain-name omnisecu.com OmniSecuR1(config)#exit OmniSecuR1#
• To configure Hostname on OmniSecuR2 use the following commands.
Router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)#hostname OmniSecuR2 OmniSecuR2(config)#exit OmniSecuR2#
• To configure Domain name on OmniSecuR2, use the following commands.
OmniSecuR2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR2(config)#ip domain-name omnisecu.com OmniSecuR2(config)#exit
Step 2: Configure Pre-Shared Key on IPSec Peers
We have three methods of device authentication, Pre-Shared Key, RSA and Digital Certificates. Pre-Shared Key is the simplest among the three to set-up. The term Pre-Shared Key means a common key pre configured on both IPSec peers. We use Pre-Shared keys only if we have small number of IPSec devices. As the number IPSec devices grow, we may move to Digital Certificates for better scalability and security.
• To configure a Pre-Shared Key in OmniSecuR1 (for OmniSecuR2), use the following commands.
OmniSecuR1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR1(config)#crypto isakmp key 0 OmniSecuDotCom address 192.168.0.2 OmniSecuR1(config)#exit OmniSecuR1#
Please note that the Pre-Shared key we are using here is OmniSecuDotCom
The 0 before the Pre-Shared key specifies that the key is not encrypted.
• To configure a Pre-Shared Key in OmniSecuR2 (for OmniSecuR1), use the following commands.
OmniSecuR2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR2(config)#crypto isakmp key 0 OmniSecuDotCom address 192.168.0.1 OmniSecuR2(config)#exit OmniSecuR2#
Step 3: Define one or more ISAKMP Policies
An ISAKMP (IKE) policy is used to define the components of Phase1 ISAKMP management connection. An ISAKMP policy defines how Phase1 ISAKMP (IKE) tunnel is to be created, authenticated, and protected. It is possible to have more than one ISAKMP policy on a Router. If we have multiple IPSec connection to multiple sites and the Routers on different sites have different specifications and different abilities we must define multiple ISAKMP policies for different sites.
In this example we are going to define only one policy.
An ISAKMP (IKEv1) policy contains the parameters used for IKEv1 Phase 1 negotiation. Following are the Parameters and the selected Parameters which we are going to configure for this example.
Please note that the available Parameters may change depending on the version of IOS which you use. I am using IOS Version 15.2(4).
| Type | Possible Parameters | Selected Parameter |
|---|---|---|
| Priority Number | 1-10000 | 1 |
| Encryption Algorithm | DES, 3DES, AES128, AES192, AES256 | AES256 |
| Hashing Algorithm | MD5, SHA1, SHA256, SHA384, SHA512 | SHA512 |
| Diffie-Hellman Group | 1, 2, 5, 14, 15, 16, 19, 20, 21, 24 | 24 |
| Authentication Method | PRE-SHARE, RSA-ENCR, RSA-SIG | PRE-SHARE |
| Connection lifetime (Seconds) | 60-86400 | 21600 |
• To configure a ISKAMP policy in OmniSecuR1 (with the selected values as in above table), use the following commands.
OmniSecuR1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR1(config)#crypto isakmp policy 1 OmniSecuR1(config-isakmp)#encryption aes 256 OmniSecuR1(config-isakmp)#hash sha512 OmniSecuR1(config-isakmp)#group 24 OmniSecuR1(config-isakmp)#authentication pre-share OmniSecuR1(config-isakmp)#lifetime 21600 OmniSecuR1(config-isakmp)#exit OmniSecuR1(config)#exit OmniSecuR1#
• To configure a ISKAMP policy in OmniSecuR2 (with the selected values as in above table), use the following commands.
OmniSecuR2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR2(config)#crypto isakmp policy 1 OmniSecuR2(config-isakmp)#encryption aes 256 OmniSecuR2(config-isakmp)#hash sha512 OmniSecuR2(config-isakmp)#group 24 OmniSecuR2(config-isakmp)#authentication pre-share OmniSecuR2(config-isakmp)#lifetime 21600 OmniSecuR2(config-isakmp)#exit OmniSecuR2(config)#exit OmniSecuR2#
Step 4: Define Crypto ACL to identify IPSec secured traffic
Crypto ACL is just an ACL created using normal ACL syntax, with permit or deny statements. Crypto ACLs are not used to permit or deny traffic similar to normal ACLs. In Crypto ACL, a permit statement is used to identify the traffic which is to be secured using IPSec and a deny statement is used to identify the traffic whish doesn't need to be secured. Here we are using "named extended access lists".
New to Access Control Lists (ACLs)? Please refer below lessons if you wish.
Introduction to Access Control Lists (ACL)
Standard Access Control Lists (ACLs)
Where should a Standard Access Control List (ACL) be placed
Access Control List (ACL) - Wildcard Masks
How to create and configure Standard Access Control Lists (ACLs)
Extended Access Control Lists (ACLs)
Where should an Extended Access Control List (ACL) be placed
Extended Access Control List (ACL) - Operators
Extended Access Control List (ACL) - TCP and UDP port numbers and names
Extended Access Control List (ACL)- established Keyword
How to create and configure Extended Access Control Lists (ACLs)
How to create and configure Access Control Lists (ACLs) for vty lines (telnet and ssh)
Named Access Control Lists (ACLs)
How to create and configure Standard Named Access Control Lists (ACLs)
How to create and configure Extended Named Access Control List (ACL)
How to edit a Named Access Control List (ACL) on router
• To configure a Crypto ACL in OmniSecuR1 (to identify the traffic to OmniSecuR2), use the following commands.
OmniSecuR1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR1(config)#ip access-list extended SITE1-SITE2-CACL OmniSecuR1(config-ext-nacl)#permit ip 172.16.0.0 0.0.255.255 172.17.0.0 0.0.255.255 OmniSecuR1(config-ext-nacl)#exit OmniSecuR1(config)#exit OmniSecuR1#
• To configure a Crypto ACL in OmniSecuR2 (to identify the traffic to OmniSecuR1), use the following commands.
OmniSecuR2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR2(config)#ip access-list extended SITE2-SITE1-CACL OmniSecuR2(config-ext-nacl)#permit ip 172.17.0.0 0.0.255.255 172.16.0.0 0.0.255.255 OmniSecuR2(config-ext-nacl)#exit OmniSecuR2(config)#exit OmniSecuR2#
Step 5: Define Transform Sets for Phase 2 negotiation
A Transform set is used to define how the data traffic between IPSec peers is going to be protected in Phase 2. It is possible to have more than one Transform Set on a Router. If we have multiple IPSec connection to multiple sites and the Routers on different sites have different specifications and different abilities we must define multiple Transform Sets for different sites.
A Transform Set must have a unique identifier name. A Transform Set can contain up to four transforms. Following are the parameters possible for a Transform Set.
| Type | Possible Parameters | Selected Parameter |
|---|---|---|
Authentication Header (AH) |
ah-md5-hmac (AH-HMAC-MD5 transform) ah-sha-hmac (AH-HMAC-SHA transform) ah-sha256-hmac (AH-HMAC-SHA256 transform) ah-sha384-hmac (AH-HMAC-SHA384 transform) ah-sha512-hmac (AH-HMAC-SHA512 transform) |
Not Applicable here |
ESP Authentication |
esp-md5-hmac (ESP transform using HMAC-MD5 auth) esp-sha-hmac (ESP transform using HMAC-SHA auth) esp-sha256-hmac (ESP transform using HMAC-SHA256 auth) esp-sha384-hmac (ESP transform using HMAC-SHA384 auth) esp-sha512-hmac (ESP transform using HMAC-SHA512 auth) |
esp-sha512-hmac |
ESP Encryption |
esp-3des (ESP transform using 3DES(EDE) cipher (168 bits)) esp-aes (ESP transform using AES cipher) esp-des (ESP transform using DES cipher (56 bits)) esp-gcm (ESP transform using GCM cipher) esp-gmac (ESP transform using GMAC cipher) |
esp-aes |
Compression |
comp-lzs (IP Compression using the LZS compression algorithm) | Not Applicable here |
• To define a Transform Set in OmniSecuR1 (for securing Phase 2 with OmniSecuR2), use the following commands.
OmniSecuR1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR1(config)#crypto ipsec transform-set SITE2TS esp-sha512-hmac esp-aes OmniSecuR1(cfg-crypto-trans)#exit OmniSecuR1(config)#exit OmniSecuR1#
• To define a Transform Set in OmniSecuR2 (for securing Phase 2 with OmniSecuR1), use the following commands.
OmniSecuR2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. OmniSecuR2(config)#crypto ipsec transform-set SITE1TS esp-sha512-hmac esp-aes OmniSecuR2(cfg-crypto-trans)#exit OmniSecuR2(config)#exit OmniSecuR2#
Step 6: Define Crypto Maps
Crypto Maps are used to connect all the pieces of IPSec configuration together. A Crypto Map consists of one or more entries. A Crypto Map is made up of Crypto ACL, Transform Set, Remote Peer, the lifetime of the data connections etc.
• To define a Crypto Map in OmniSecuR1, use the following commands.
OmniSecuR1(config)#crypto map SITE2CMAP 10 ipsec-isakmp OmniSecuR1(config-crypto-map)#set security-association lifetime seconds 3600 OmniSecuR1(config-crypto-map)#set peer 192.168.0.2 OmniSecuR1(config-crypto-map)#set transform-set SITE2TS OmniSecuR1(config-crypto-map)#set pfs group16 OmniSecuR1(config-crypto-map)#match address SITE2CACL OmniSecuR1(config-crypto-map)#exit OmniSecuR1(config)#exit
• To define a Crypto Map in OmniSecuR2, use the following commands.
OmniSecuR2#configure terminal OmniSecuR2(config)#crypto map SITE1CMAP 10 ipsec-isakmp OmniSecuR2(config-crypto-map)#set security-association lifetime seconds 3600 OmniSecuR2(config-crypto-map)#set peer 192.168.0.1 OmniSecuR2(config-crypto-map)#set transform-set SITE1TS OmniSecuR2(config-crypto-map)#set pfs group16 OmniSecuR2(config-crypto-map)#match address SITE1CACL OmniSecuR2(config-crypto-map)#exit OmniSecuR2(config)#exit OmniSecuR2#
Step 7: Activate Crypto Maps by applying the Crypto Map to Router's Interface
• To apply Crypto Map to the WAN Interface on OmniSecuR1, use following commands.
OmniSecuR1#configure terminal OmniSecuR1(config)#interface gi0/0 OmniSecuR1(config-if)#crypto map SITE2CMAP OmniSecuR1(config-if)#exit OmniSecuR1(config)#exit OmniSecuR1#
• To apply Crypto Map to the WAN Interface on OmniSecuR2, use following commands.
OmniSecuR2#configure terminal OmniSecuR2(config)#interface gi0/0 OmniSecuR2(config-if)#crypto map SITE1CMAP OmniSecuR2(config-if)#exit OmniSecuR2(config)#exit OmniSecuR2#
After configuring, initiate an IP traffic from device inside at Site-1 network to reach a device at Site-2 network. Your IPSec VPN Main mode IPSec tunnel will be built when any router find interesting traffic.