Hash values, MAC and HMAC in SSH
The purpose of Hashing algorithms, MAC (Message Authentication Code) and HMAC (Hashed Message Authentication Code) in SSH is for validating whether the received packets are from the real original sender and the data packets are not tampered/corrupted during network transit.
Hash Values
Hashing algorithms are used to generate Hash values from a chunk of data. Hashing algorithms generate a unique Hash string as output, taking a chunk of data as the input. Modifying even a single bit of the data will result in generating an entirely different Hash value, next time when you run the same Hashing algorithm on that data again. The output string of a Hashing algorithm is generally called as a Hash value.
In SSH, Hash values are mainly used for checking data integrity (data is not modified accidently or intentionally), and to verify the authenticity of communication. The main use of Hash values in SSH is with HMAC (Hashed Message Authentication Code). HMAC uses Hash values to generate HMAC codes. These are used to ensure that the received message text is intact and unmodified.
Please find some points about Hash values bullet pointed below.
- The chunk of data on which the Hashing algorithm is run, can be of any length/size. But the output of a particular Hash value string generated by a particular Hashing algorithm, will be of fixed length.
- Unlike Encryption algorithms, Hashing algorithms are not reversible. Meaning is that, it is theoretically impossible to find the original data from Hash value strings.
- The incident of getting same Hash value for two different data contents is called as Hash value collision. For newer Hashing algorithms, theoretically it is impossible for a Hash value collision to happen.
Important Hashing Algorithms
- MD4 (Message Digest 4) : MD4 was invented by Ron Rivest of RSA Security LLC. MD4 produces a 128–bit Hash value string. MD4 is no longer considered secure.
- MD5 (Message Digest 5) : MD5 was also invented by Ron Rivest of RSA Security LLC. MD5 also has a 128–bit hash, and considered much secure than MD4.
- SHA or SHA-0 (Secure Hashing Algorithm) : SHA was invented by NSA to be used with the Digital Signature Standard (DSS). SHA generates a 160-bit Hash value.
- SHA–1 : SHA–1 also generates a 160–bit hash value. SHA–1 corrected security flaw in SHA–0 that made it susceptible to attacks.
- SHA–2 : SHA–2 is a family of Hashing algorithms. SHA–224 (224–bit Hash value), SHA–256 (256–bit Hash value), SHA–384 (384–bit Hash value), SHA–512 (512–bit Hash value), SHA–512/224 (224–bit Hash value), SHA–512/256 (256–bit Hash value).
- SHA–3 : SHA–3 is also a family of Hashing algorithms. SHA3–224 (224–bit Hash value), SHA3-256 (256–bit Hash value), SHA–384 (384–bit Hash value), SHA3–512 (512–bit Hash value).
- RIPEMD–160 : RIPEMD–160 is a more secure version of the RIPEMD (RIPE Message Digest) Hashing algorithm, which generates 160–bit Hash value.
How Hash values work
How Hash values work in finding the integrity of data? If you want to test the integrity of a file in future, calculate and keep the Hash value string, using any good Hashing algorithm. Later, if you want to check the data is not changed since you calculated the Hash value last time, run the same Hashing algorithm on the same data again and compare the Hash value string output with previous Hash value string output. If both are same, then the data is not changed between the two calculations. SSH protocol sends Hash values (actually a modified type, called as HMAC) along with SSH packets to detect whether the data is changed during network transit.
Let us try to understand how Hash values work, by doing a small exercise.
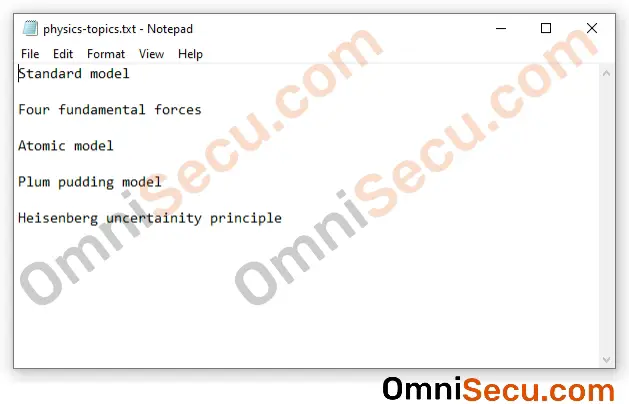
I have a small text file in my folder, physics-topics.txt. The contents of the text file is as shown below.
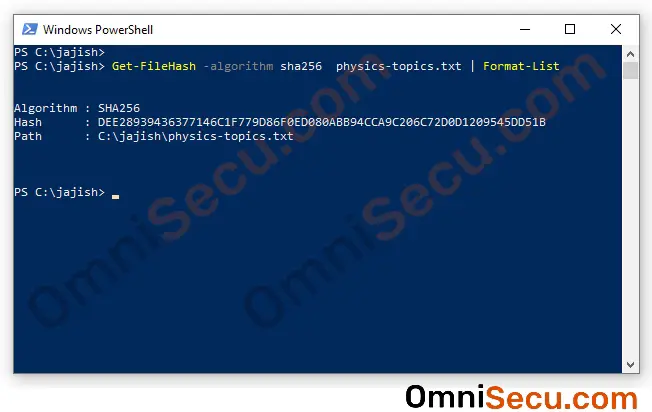
Open PowerShell in your Windows 10 machine, by typing PowerShell at search box and clicking PowerShell on search results. Change working directory to where you have saved the file. Run following PowerShell command to calculate the SHA–256 Hash of the saved file. Remember to change the name of the file "physics-topics.txt" to the name of the file in your folder.
Get-FileHash -algorithm sha256 physics-topics.txt | Format-List
You can see the SHA–256 Hash value output, as shown below.
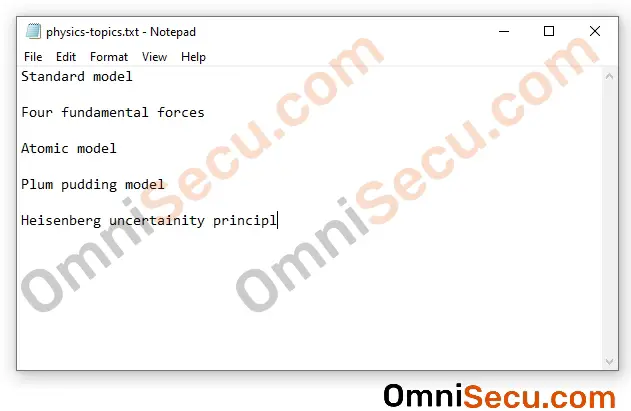
Now, I have deleted the last character of the content of file, as shown below, and saved the file.
Again, the SHA–256 Hash value is calculated using the above command, as shown below.
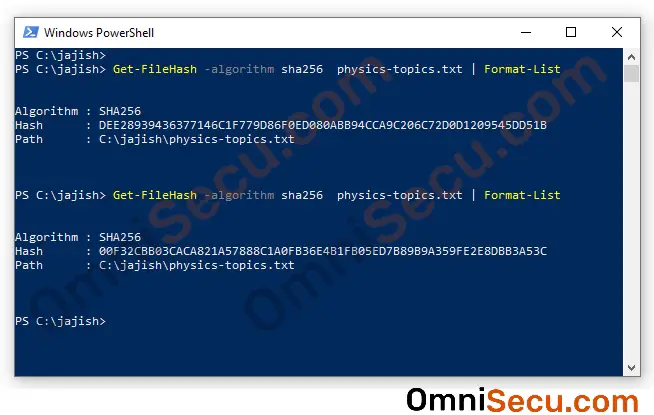
You can see that the Hash value has changed completely, even for a change in one character. Hash values are very useful in finding the data integrity of secure communication protocols like SSH.
Hash value alone is not useful in calculating the integrity data while in network transit. Because, any malicious user in the middle can capture the packet, alter the contents of the original data, recalculate new Hash value and forward it to the recipient. When the real recipient calculates the Hash again, he will find the Hash string is matching and will never notice that the data is tampered.
In SSH, to make Hashing algorithms to work in a more secure way, HMAC (Hashed Message Authentication Code) is used.
MAC (Message Authentication Code)
Message Authentication Code (MAC) is a way to validate the sender and to check data integrity. Note that a shared symmetric secret key must be established between sender and receiver before, for this to work. Only the sender and the receiver have the shared symmetric secret key in possession, not anyone else.
The sender concatenates the shared symmetric secret key with the original message. Hash value (MAC value) is calculated for both the message and the shared symmetric secret key. The calculated Hash value (MAC value) is also sent along with encrypted message to the receiver. Note that only message is sent to the recipient, shared symmetric secret key is not sent via network. When the packet reaches at the receiver side, the receiver concatenates the shared symmetric secret key with the received message (after decrypting it), and the Hash value is again calculated using the same Hashing algorithm.
If the MAC generated at the receiver and the MAC received from the sender matches, the receiver can assure that the message is sent from the authenticated real sender, not from an intruder or a malicious user. The receiver can also make sure that the message is not tampered on transit, because only the sender and the receiver have the secret key in possession. Note that in SSH the data packets are transferred encrypted, using the shared symmetric secret key established at the beginning steps of SSH. Please visit following link to learn how SSH works.
HMAC (Hashed Message Authentication Code)
HMAC (Hashed Message Authentication Code) is a more secure way to validate the sender and also to check data integrity. HMAC codes provide better security, hence used in SSH. HMAC (Hashed Message Authentication Code) computes the hashes two times. Two keys are derived from the shared symmetric secret key, called as the inner key and the outer key. The first calculation of Hash value is done using the message and the inner key to generate an internal hash value. A final Hash value is generated at second calculation using the inner hash result and the outer key.
We have discussed about symmetric shared symmetric secret key many times before. For HMAC to work, the sender and receiver must have the same shared symmetric secret key in possession. HMAC itself does not provide any way to establish a symmetric shared secret key between sender and receiver. To establish a shared symmetric key between two parties, asymmetric encryption algorithms like DH (Diffie-Hellman) key exchange, or RSA key exchange is used.
Click following link to learn what are Symmetric Encryption and Asymmetric Encryption.
Any Hashing algorithm can be used in the calculation of an HMAC. For example, if SHA-384 Hashing algorithm is used, we will call it as HMAC-SHA-384.
Following are some examples; HMAC-MD5, HMAC-SHA-1, HMAC-SHA-256, HMAC-SHA-384, HMAC-SHA-512.
HMAC value in real SSH packet
Okay, Are you curious how HMAC value appear in a real captured SSH packet? See below image.
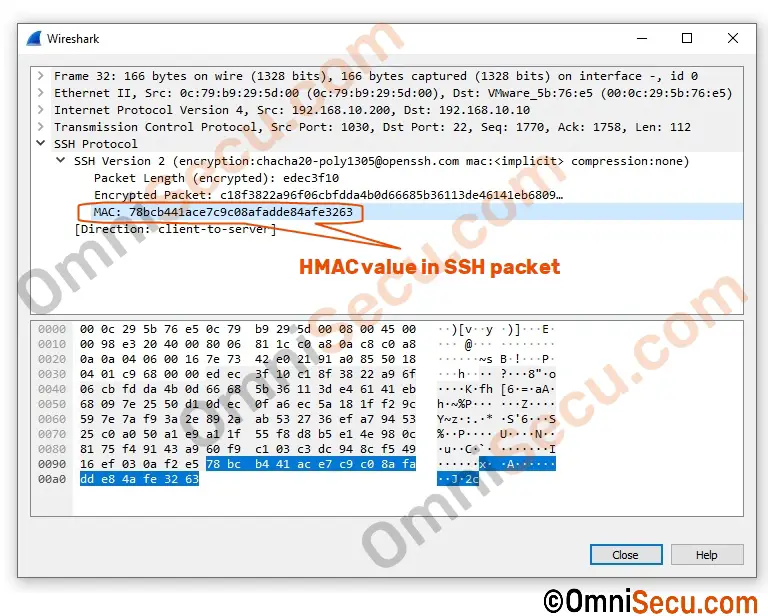
Note that the cipher negotiated and used in this particular implementation of SSH (OpenSSH SSH Server for Windows Server) is chacha20-poly1305. The HMAC in this capture image is of Poly1305.