SSH Encryption Algorithms
What are Plain Text and Cipher Text
We have learned in previous lessons that SSH encrypts network traffic to prevent eavesdropping. The first set of keywords you have to remember is, Plain Text and Cipher Text. Any data in its original format is called as Plain Text. Cipher Text is the scrambled version of Plain Text, which is meaningless to a third-party.
What are Encryption and Decryption
Next set of keywords are Encryption and Decryption. Encryption is the process of converting Plain Text to Cipher Text. In other words, scrambling Plain Text. Decryption is just the reverse process, converting back the meaning-less Cipher Text to its original Plain Text format.
What are Encryption algorithm and Encryption key
An Encryption algorithm is the logic behind converting Plain Text to Cipher Text. Encryption Key is usually a long string. Encryption algorithms use an Encryption Key to encrypt data. You need the same key (For Symmetric Encryption), or a mathematically related key (for Asymmetric encryption) to decrypt the scrambled data back to original Plain Text format. Even if someone knows the encryption algorithm used for encrypting the Plain Text, without Encryption key, it is impossible to convert the scrambled data (Cipher Text) to its Plain Text version.
Symmetric Encryption algorithms and Asymmetric Encryption algorithms
The third set of key words related with cryptography are Symmetric Encryption algorithms and Asymmetric Encryption algorithms.
Symmetric Encryption algorithms
A Symmetric Encryption algorithm uses the same key for Encryption and Decryption. For example; If during encryption you had selected "OMNISECU" as the Symmetric Encryption key to convert Plain Text to Cipher Text. During Decryption, you need to provide the same key "OMNISECU" to covert back Cipher Text to Plain Text.
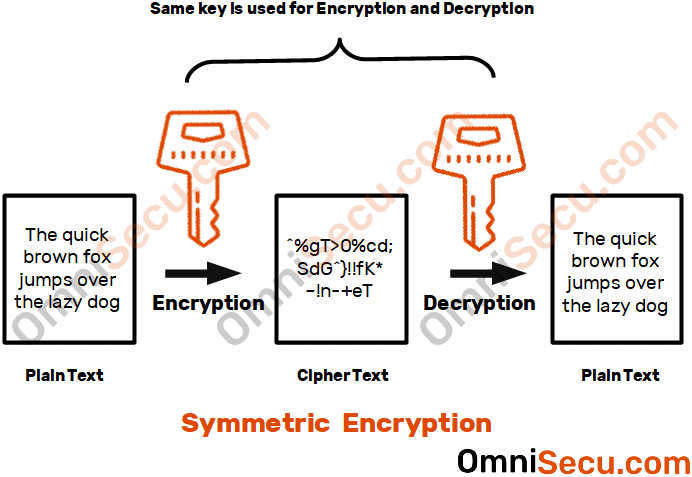
Some examples of Symmetric Encryption algorithms are AES (Advanced Encryption Standard), Salsa20 / ChaCha20, 3DES (Triple Data Encryption Algorithm), IDEA (International Data Encryption Algorithm) and Blowfish.
Asymmetric Encryption algorithms
Asymmetric Encryption algorithms use a set of Keys, normally referred as public key and private key. Public key and private key are mathematically related keys. The Data encrypted with one key can be decrypted only with its mathematically related key. In public key encryption, public key can be distributed to anyone who is requesting the public key. The data encrypted with public key can only decrypted with its related private key, which is kept highly secured at the computer who owns the key pair.
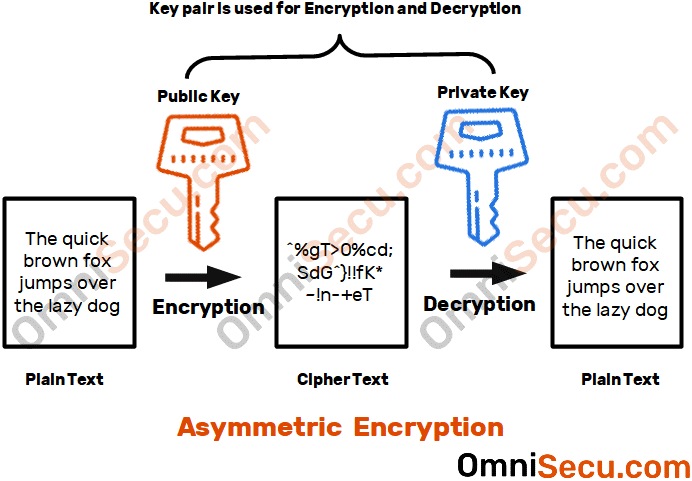
Some examples of Asymmetric Encryption algorithms are RSA (Rivest–Shamir–Adleman), ECC (Elliptic Curve Cryptography), DH (Diffie-Hellman), El Gamal, ECDH (Elliptic Curve Diffie-Hellman) and ECDSA (Elliptic Curve Digital Signature Algorithm).
Encryption algorithms in SSH
Asymmetric Encryption algorithms work slower than Symmetric Encryption algorithms. Asymmetric Encryption algorithms require much more computing power than Symmetric Encryption algorithms.
Now the issue is, even though Symmetric Encryption algorithms are faster, exchanging the encryption key over the network can expose the keys to malicious users. So, SSH uses Asymmetric encryption to establish a shared symmetric secret key between SSH client and SSH server for encryption and decryption. New Symmetric Encryption keys are generated, if more data is need to be transmitted or session runs a long time, to add more security.
SSH has support for many different Symmetric and Asymmetric encryption algorithms. SSH client and SSH server negotiate between each other, the encryption algorithms to use.