How SSH works
In this lesson, let us try to understand how SSH works. For the purpose of this lesson, we are using SSH server as OpenSSH Server on Windows Server, and SSH client as PuTTY on a Windows 10 machine. The SSH protocol version used is SSH-2.
Before continuing, I strongly suggest you to visit following lessons to understand the technical terms related with SSH.
- SSH Components
- SSH Packet Format
- SSH Encryption Algorithms
- Hash values, MAC and HMAC in SSH
- What is SSH host key
An SSH secure connection is established between an SSH client and SSH server two separate stages. In first stage, the encryption algorithms and HMAC hashing algorithms are negotiated between SSH client and SSH server. Once the security protocols are negotiated, the user is authenticated through the secure encrypted SSH tunnel. Since user authentication is done via secure encrypted SSH tunnel, you are not able to see the actual Plain Text contents in captured packets.
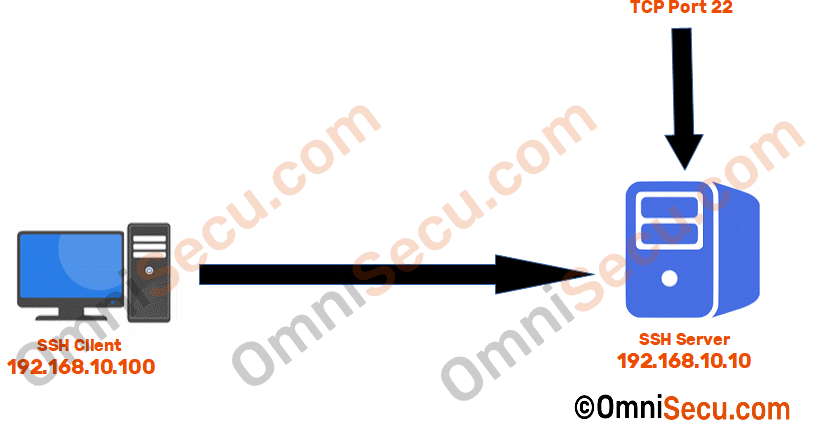
Below image shows the IP address and port number of SSH Client and SSH Server, used in this lesson to explain how SSH works.
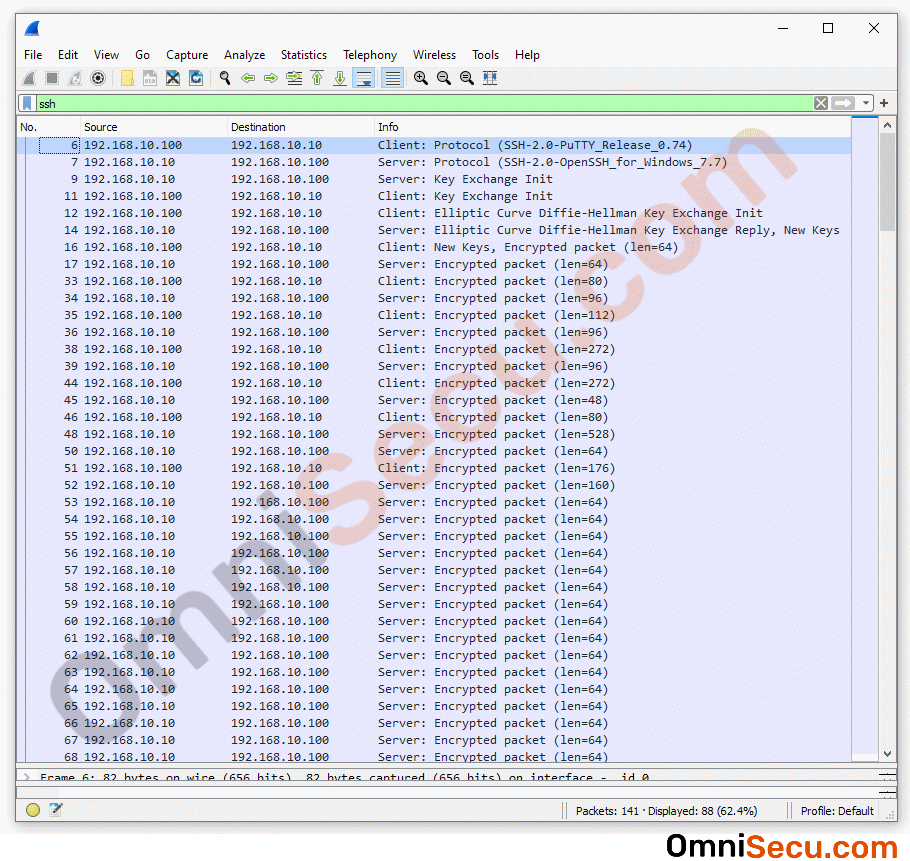
First, let us have a look at the Wireshark captured file screenshot to understand the communications between SSH client and SSH server. Below image shows a very brief explanation of how SSH works. Let us try to understand more about Packet numbers 6, 7, 9, 11, 12, 14 and 16 in below image.
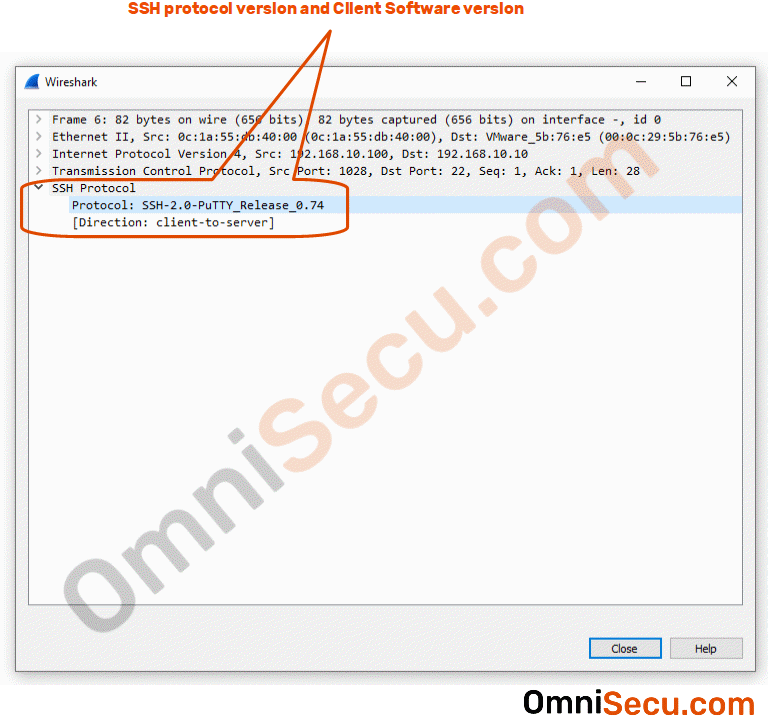
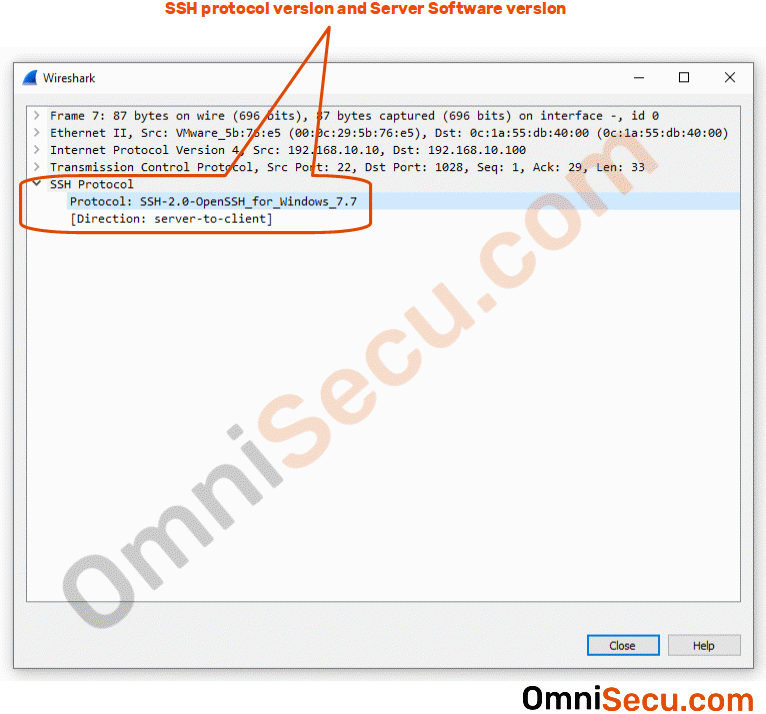
Packet number 6 : Packet number 6 is sent from SSH client to SSH server. This packet contains the SSH protocol version, information related with SSH client software and its version. Please refer below image.
Packet number 7 : Packet number 7 is sent from SSH server to SSH client. This packet contains the SSH protocol version, information related with SSH server software and its version. Please refer below image.
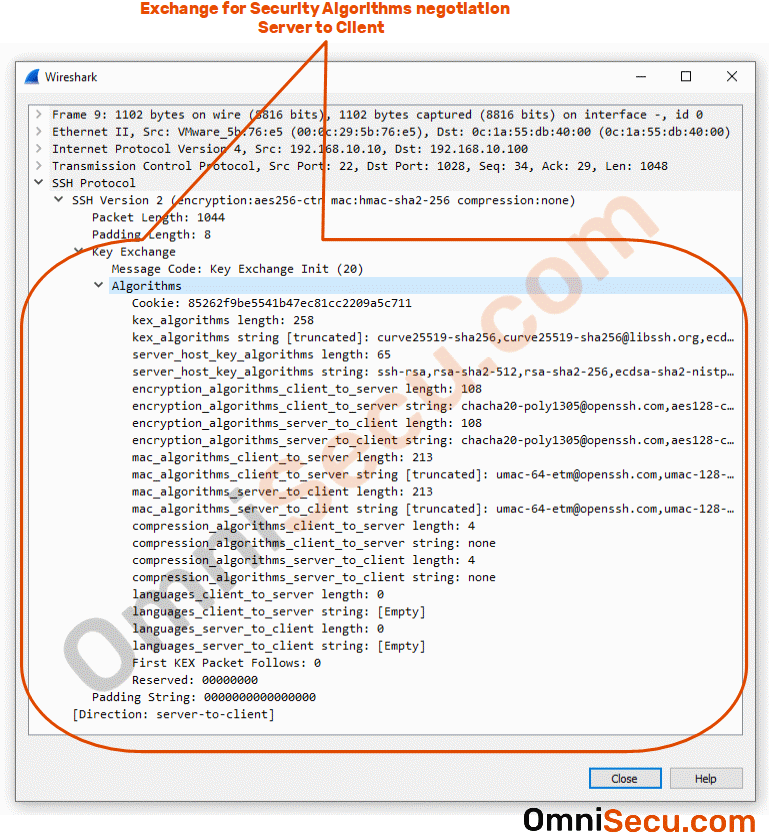
Packet number 9 : Packet number 9 is "Key Exchange Init" sent from SSH server to SSH client. This packet contains different parameters for negotiating SSH secure tunnel, like crypto algorithms, Hashing algorithms, compression algorithms (optional) etc, supported by the SSH server. Please refer below image.
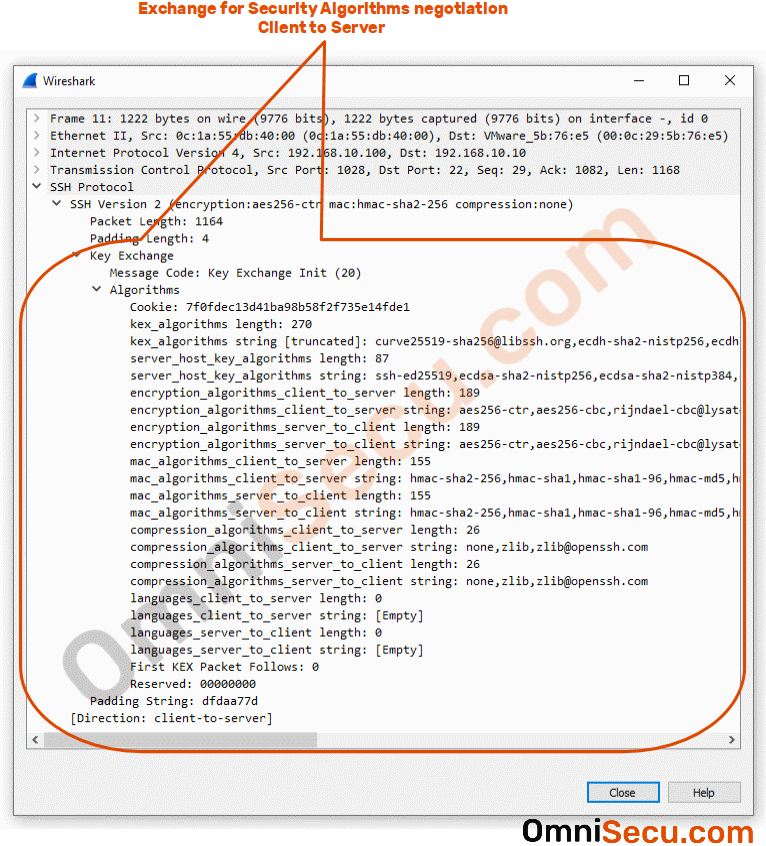
Packet number 11 : Packet number 11 is "Key Exchange Init" sent from SSH client to SSH server. This packet contains different parameters for negotiating SSH secure tunnel, like crypto algorithms, HMAC and Hashing algorithms, compression algorithms (optional) etc, supported by the SSH client. Please refer below image.
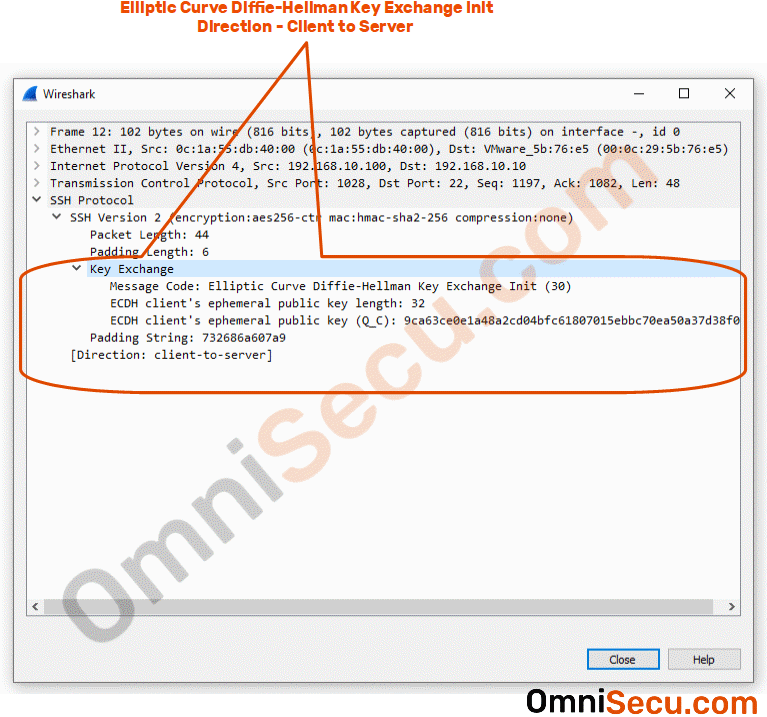
Packet number 12 : Packet number 12 is sent from SSH client to SSH server, Elliptic Curve Diffie-Hellman key exchange init. This packet contains Elliptic Curve Diffie-Hellman key exchange related info. You can also see the SSH client’s ECDH (Elliptic Curve Diffie-Hellman) ephemeral public key in the capture screenshot image. The main purpose of Elliptic Curve Diffie-Hellman key exchange init is to create a shared symmetrical secret key between SSH client and SSH server. Please refer below image.
Packet number 14 : Packet number 14 is the reply for previous message, Elliptic Curve Diffie-Hellman key exchange init. Packet number 14 is sent from SSH server to SSH client. This packet contains Elliptic Curve Diffie-Hellman key exchange related info. You can also see the SSH server’s ECDH (Elliptic Curve Diffie-Hellman) ephemeral public key in the capture screenshot image. The main purpose of Elliptic Curve Diffie-Hellman key exchange init is to create a shared symmetrical secret key between SSH client and SSH server.
Note that by using the public key from Elliptic Curve Diffie-Hellman key exchange init message, a shared symmetrical secret key is generated at SSH server. We can see a New keys message also in below image. New keys message lets the other SSH peer know that the shared symmetrical secret key is generated. Please refer below image.
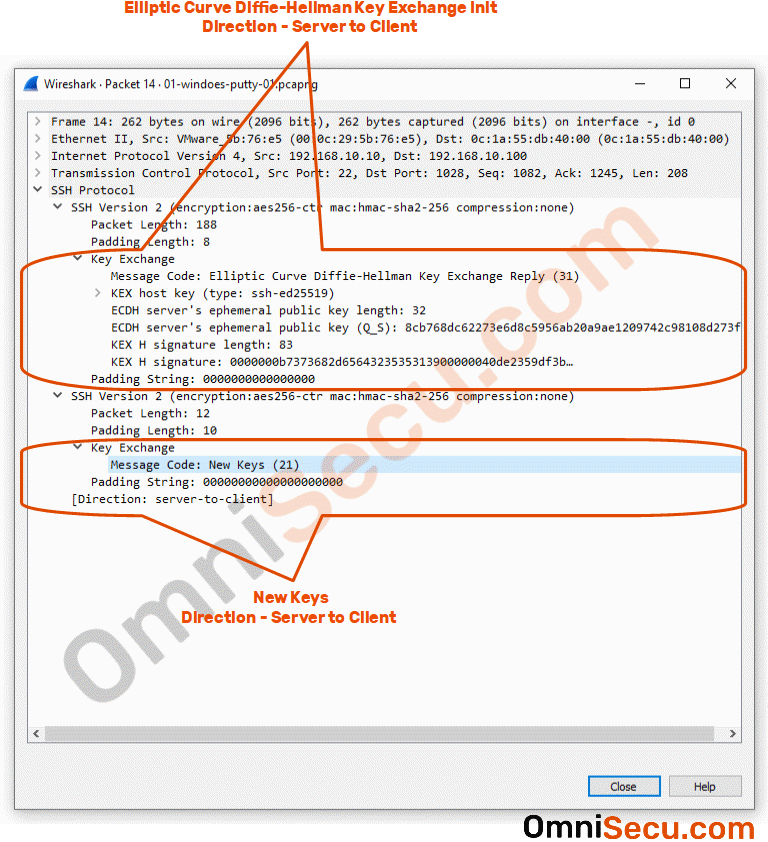
Packet number 16 : Packet number 16 is the New keys message from SSH client to SSH server. New keys message lets the other SSH peer know that the shared symmetrical secret key is generated.
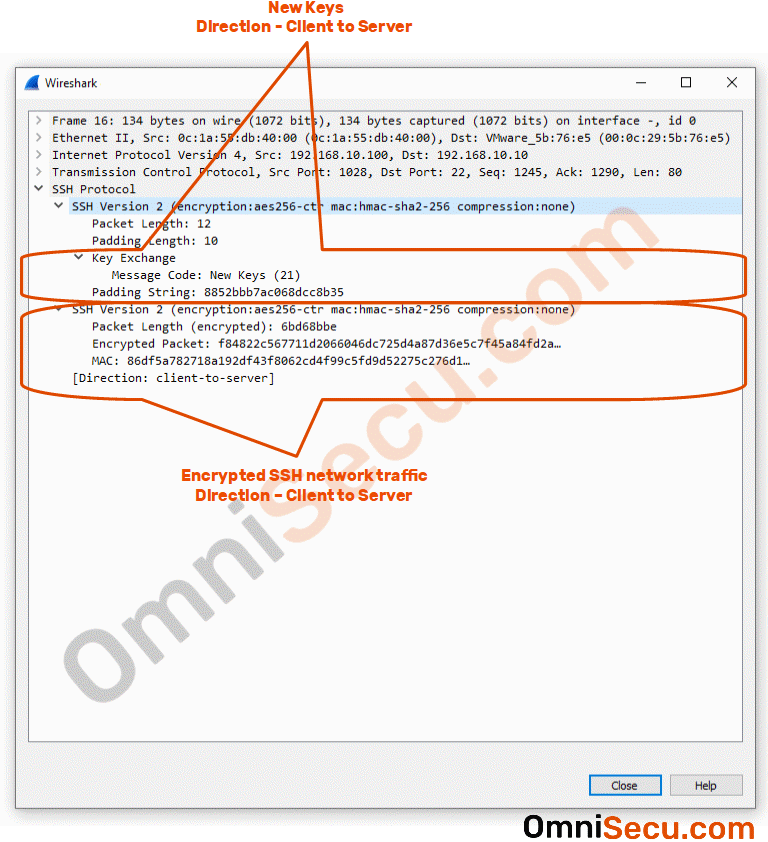
Network traffic to both sides are encrypted, once the shared symmetrical secret key is generated at both SSH client and SSH server. Now the user authentication stage starts between client and server through the secure SSH tunnel.
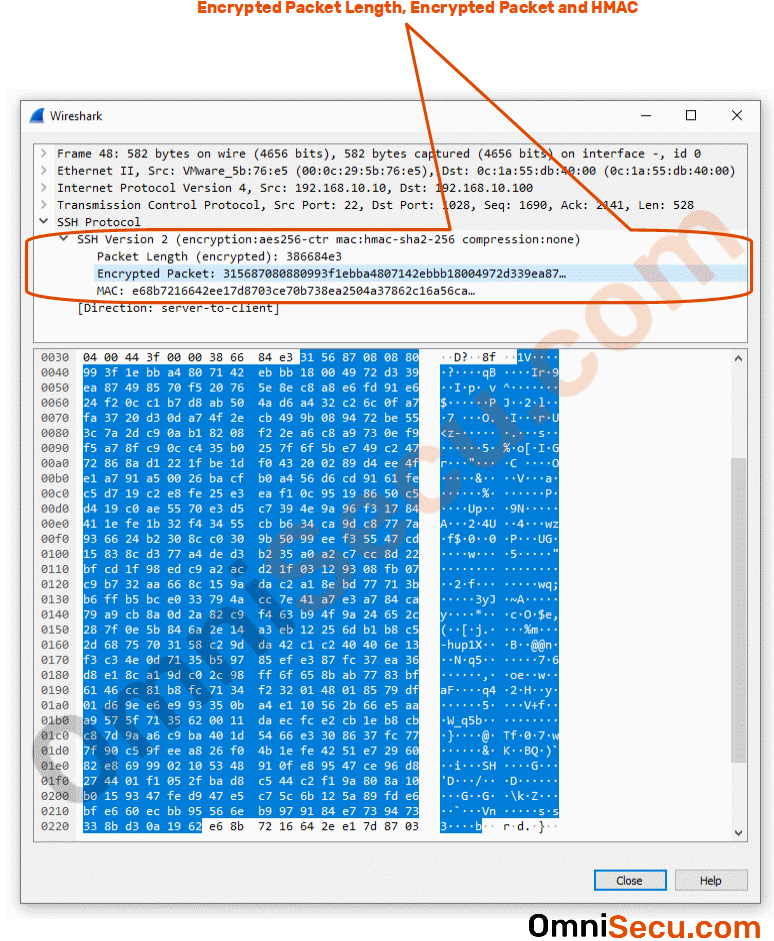
Following Wireshark packet capture screenshot shows the actual encrypted data carried by SSH-2 protocol over wire.
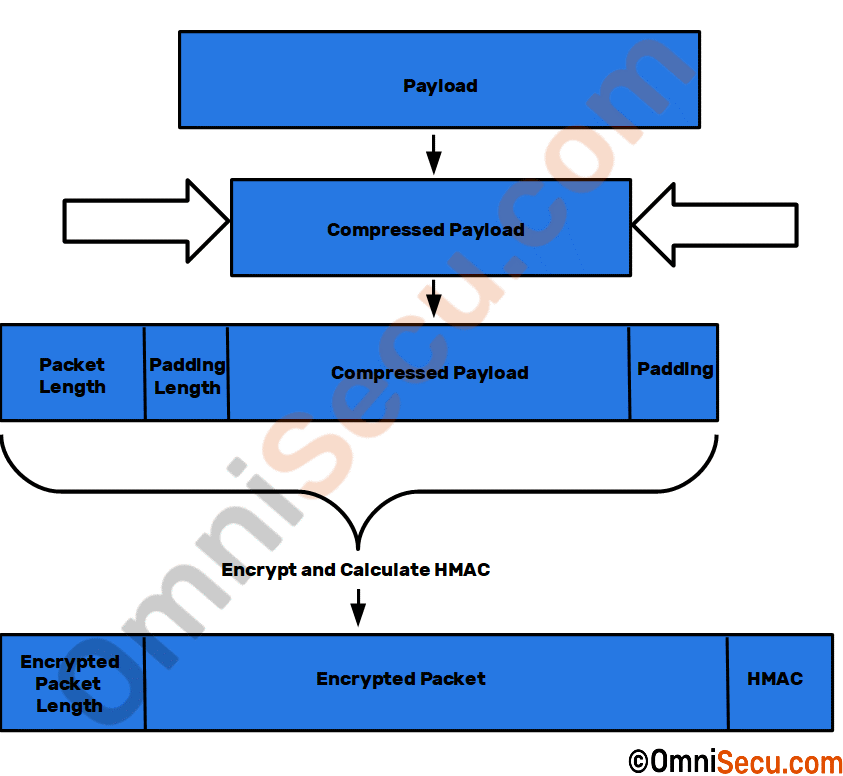
Following image shows a general depiction about how SSH data transfer works.